You need more ram and cpu power than a household router. Look on servethehome.com, build a pc based (proxmox) opnsense box, and use the flint 3 ad a wifi ap (and maybe tailscale server). Your problems will disappear.
What problems? Flint 2&3 always worked like a charm with this setup, the problem was only on previous firmware and has already been resolved…
How do you know RAM is my problem? I want to understand your thinking and reasoning. Thank you!
... because you'll have a whole new set of them that comes with FreeBSD. JFC.
The openwrt 2 (made by gl.inet) may meet the requirements for that heavy load. Once you go past a certain point, go for a pc based solution and use the flint 3 as an AP. Openwrt x86-64 is also an option
to yet be produced by GL.iNet... & I don't see anything that leads me to believe it'll have more than 1GB RAM.
@lsquare already knows these things:
Hey Bruce, unfortunately this morning I discovered that there are still leaks.
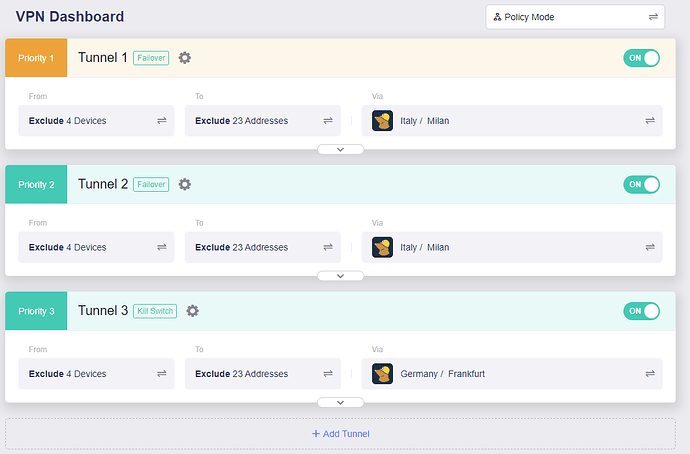
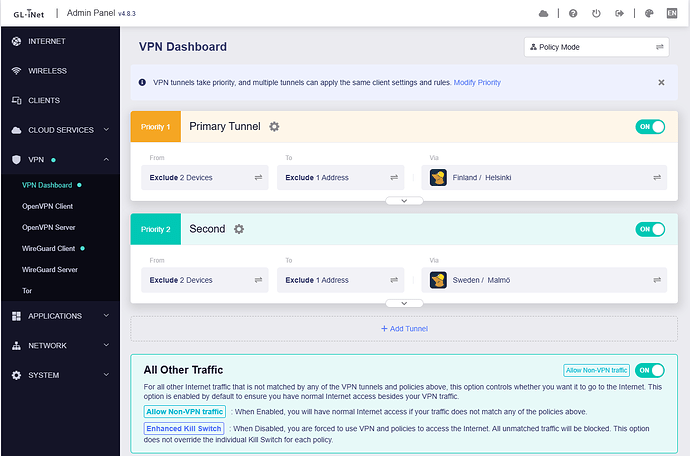
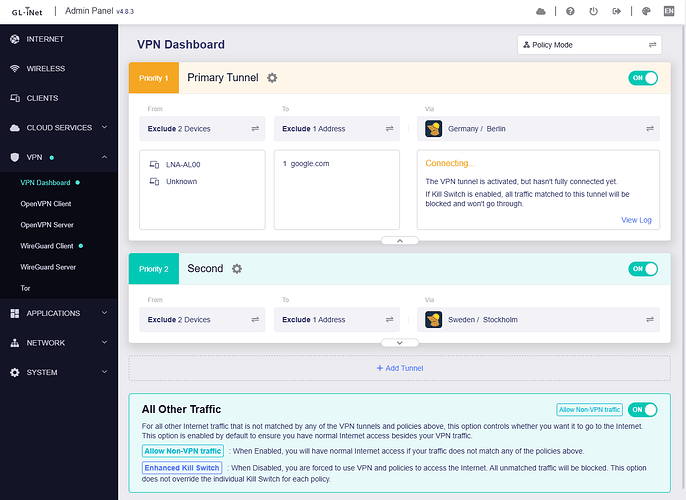
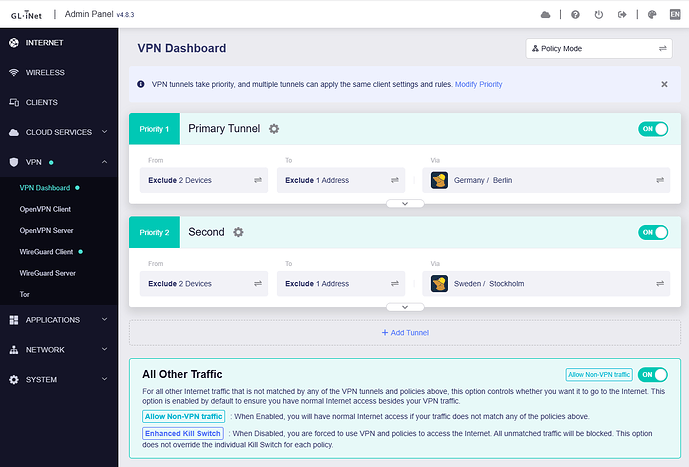
I have the following tunnels enabled:
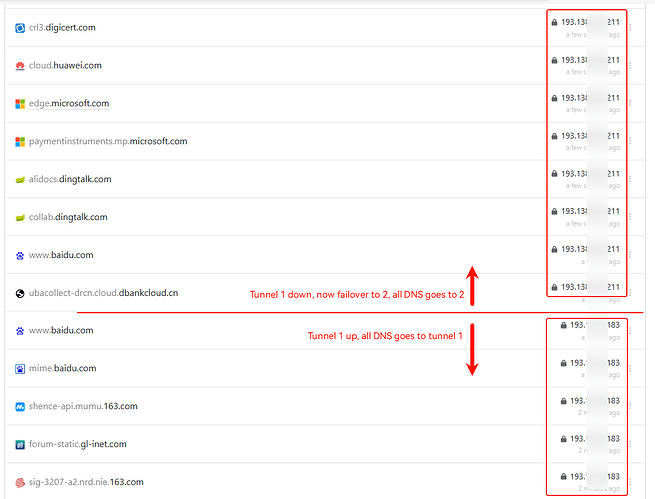
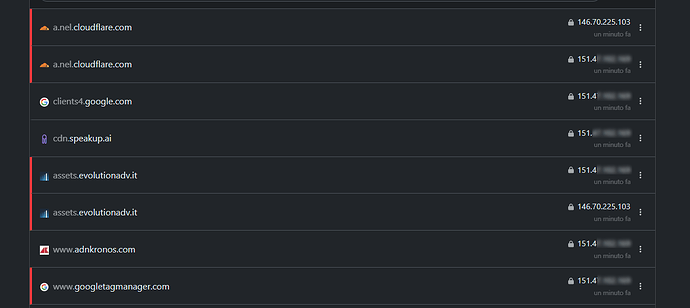
This morning Mullvad's Tunnel 1 went down so Tunnel 1 is supposed to jump to Tunnel 2 since is in failover mode. And it does, but then again in Nextdns logs I see my Wan address, not Tunnel 2 address.
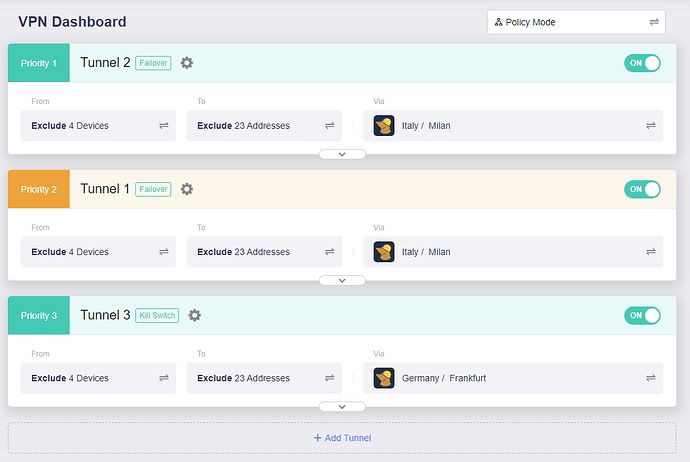
Switching priority this way everything is working normally again without leaks:
P.S.: At the moment I am using Firmware 4.8.2 Beta 2025-08-29.
Nah. Flint2 & 3 are more than enough for this setup in a home enviroment.
Yeah, obviously if you are using a lot of blocklist on Adguard Home there will be surely some problems but in this case filtering is done by NextDNS, not AdguardHome.
Setup is rock solid this way, I even reached 5 Months of continuous power-ON with Flint2 without a single problem and Flint3 is doing an excellent job too (and I have an average DNS resolution time of 7ms without any error)!
Please upgrade to the latest firmware to test again, I just tested in the v4.8.3 snapshot (09/18), there is no problem.
-
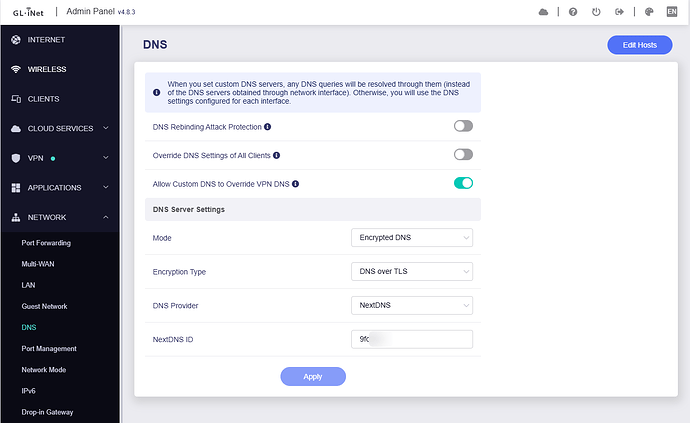
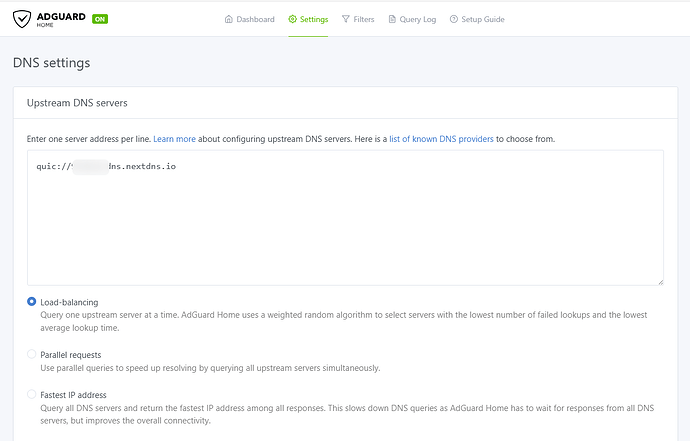
DNS server is NextDNS with my person ID:
-
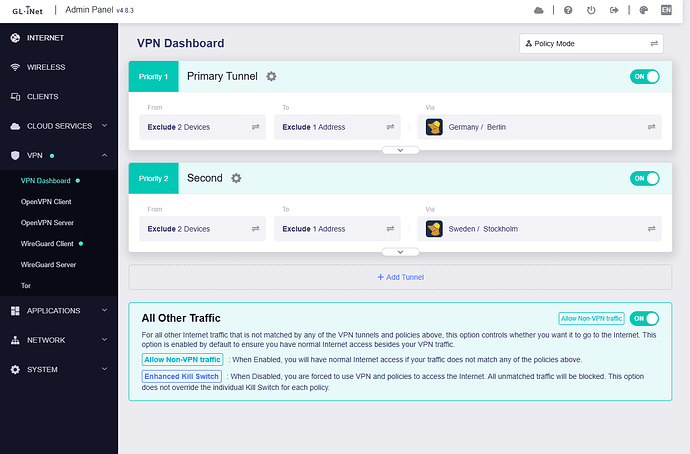
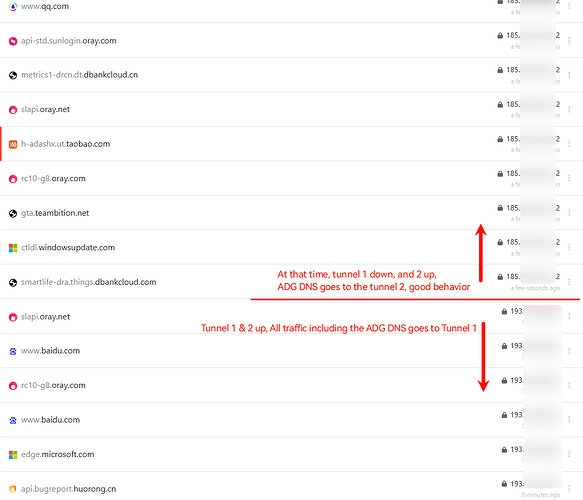
Tunnel 1 and 2 up, all traffic goes to 1
-
Tunnel 1 down and 2 up, all traffic goes to 2
-
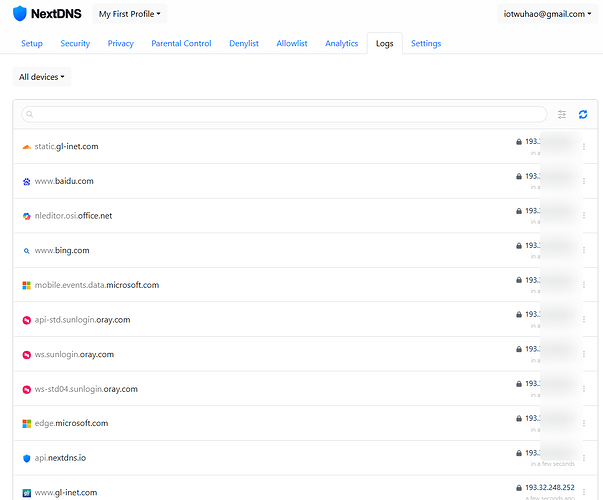
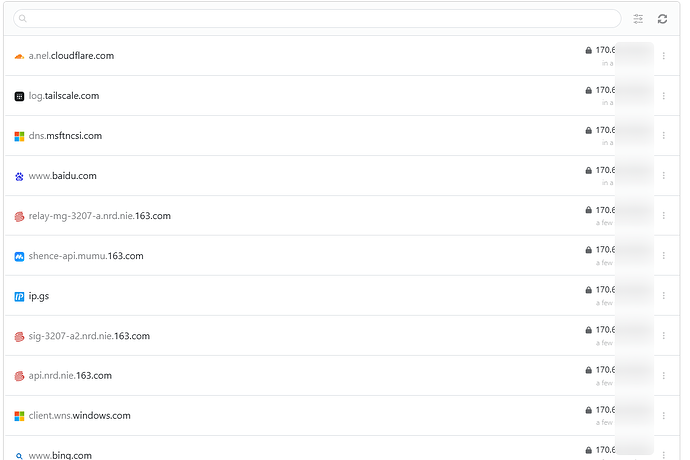
Tunnel 1 exit is 193.x.x.183, Tunnel 2 exit is 193.x.x.211, check the NextDNS log, DNS traffic without issue:
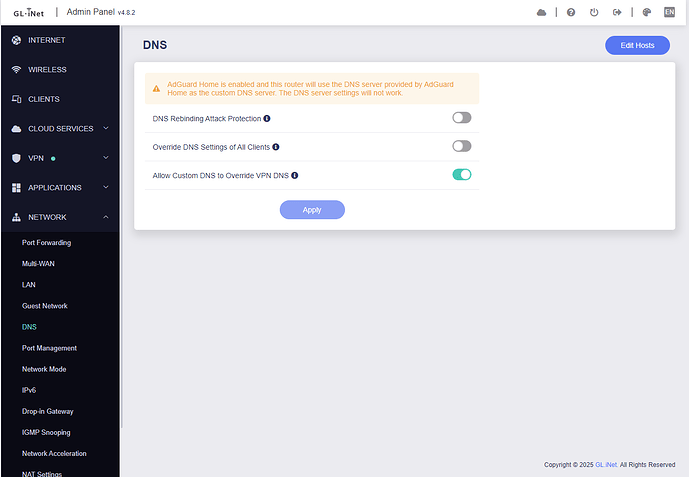
The problem arise when you're using Adguard Home, not encrypted DNS on the UI...
Anyway I'll give a try to the snapshot anyway as soon as I can...
Just tried latest snapshot 4.8.3 2025-09-22, there are definitely leaks if the first tunnel is down and has the highest priority.
Just try it with Adguard Home enabled with NextDNS as you upstream resolver.
Hello,
I did not reproduce this issue locally, ADG DNS (DoT with NextDNS) goes to the online tunnel as expected, please check your environment again.
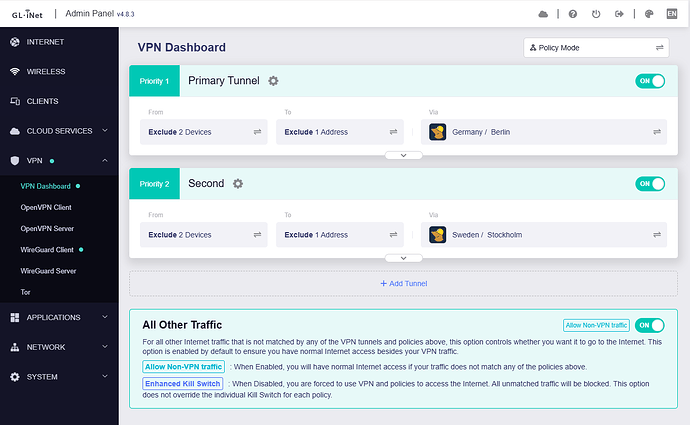
My Flint3 running snapshot v4.8.3.
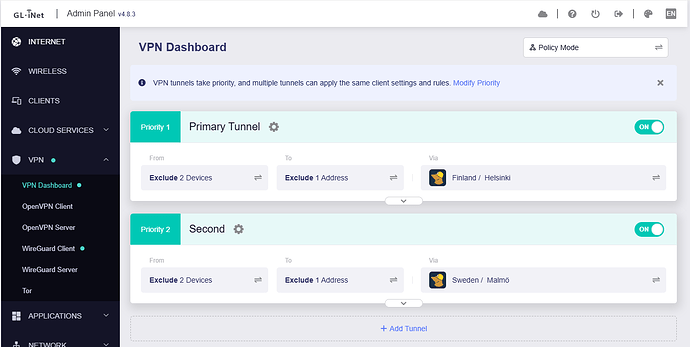
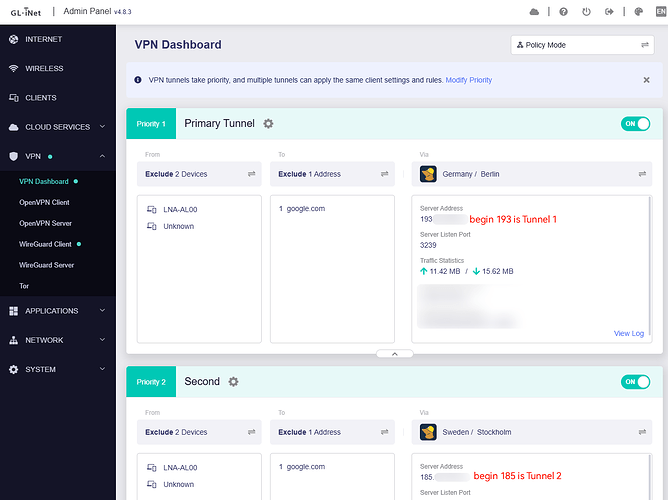
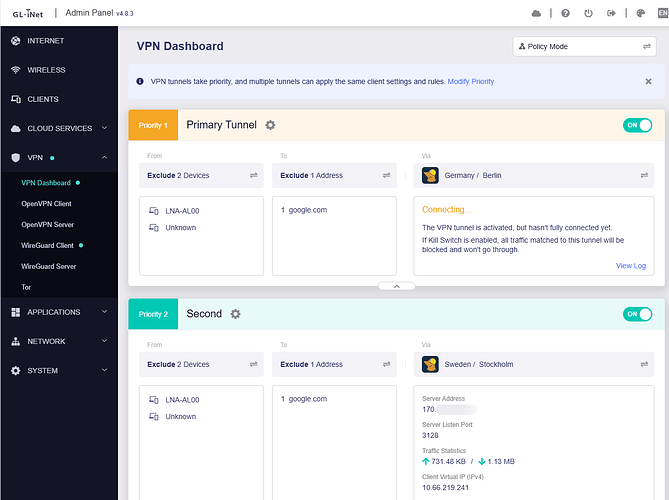
VPN Dashboard:
-
Tunnels 1 & 2 are failover
-
Tunnel 1 server IP begins 193, Tunnel 2 server IP begins 185
-
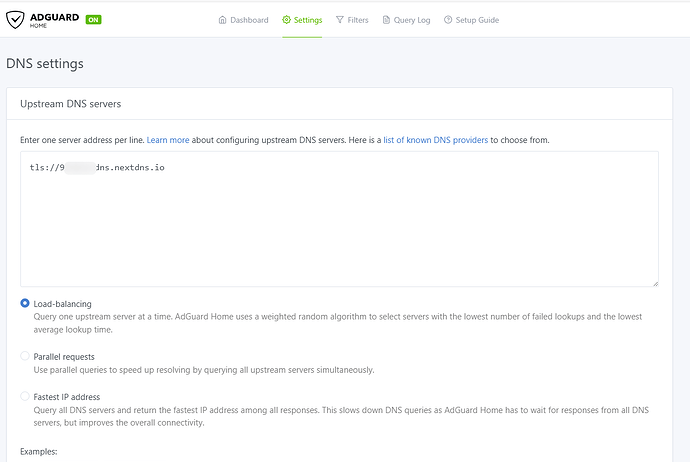
ADG Upstream DNS servers is DoT with NextDNS
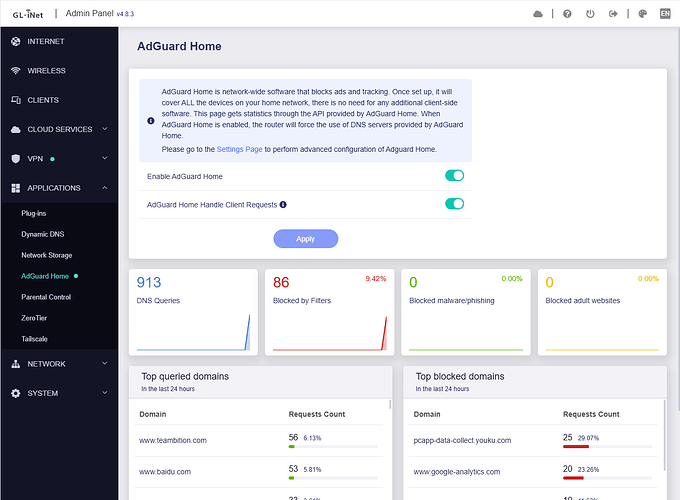
AdGuard Home Handle Client Requests enabled
-
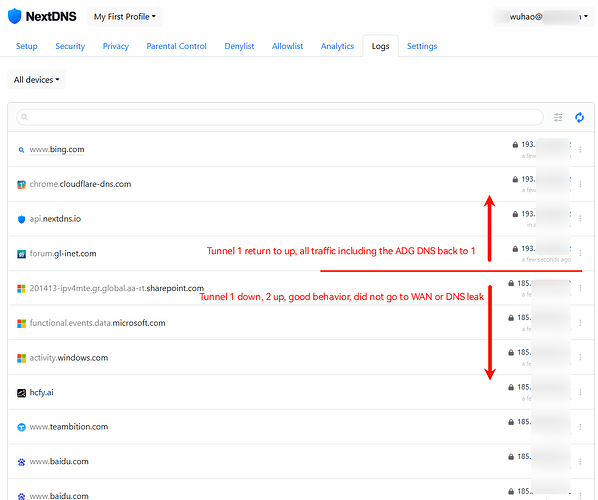
Make tunnel 1 down, ADG DNS goes to tunnel 2
-
When tunnel 1 back to up, ADG DNS back to tunnel 1 from 2
Bruce,
like the original problem of this thread, to make the leaks appear you have to test it for a certain amount of time while browsing, especially if you are using TLS. If you want to trigger it faster, just use QUIC.
For me it's still easily reproducible even after a reset and the beahviour is absolutely identical to the original post of this thread but now it happens when the first tunnel is down: at some point I have mixed IPs from WAN and WG tunnel on NextDNS logs.
Thanks for your updates.
Will check with QUIC again.
Hello,
ADG's upstream DNS server is configured as QUIC in this test, and the issue you mentioned does not reproduce.
About the domain resolutions from the WAN's DNS requests (display in your NextDNS log), are they in your VPN policy exclude list?
The server IP of Tunnel 1 starts with 193
The server IP of Tunnel 2 starts with 170
When the Tunnel1 down, all traffic includes DNS requests, go to Tunnel 2, without issue:
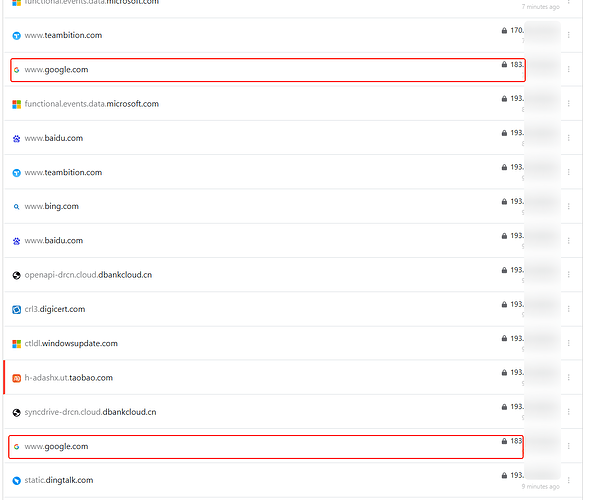
During the test period, there are 2 DNS requests google.com go to the WAN port, that is normal behavior, since in my VPN policy configuration, google.com is in the exclude list.
Thank you Bruce, sorry for the very late reply.
After checking, seems that the problem is related to upgrading Adguard Home with Admon's script.
After updating, even if an address is in policy configuration (exclude), on NextDNS logs I see my Tunnel IP instead of WAN for excluded addresses, while stock Adguard Home version from firmware shows correctly the WAN IP address... ![]()
Unfortunately I am extremely busy at work atm and I can't test it further for now...
Probably the ADG update has changed some APIs and affected dnsmasq mark to split.
If there are no special needs, I think the ADG version from the firmware is a better choice.