I can’t get it to work.
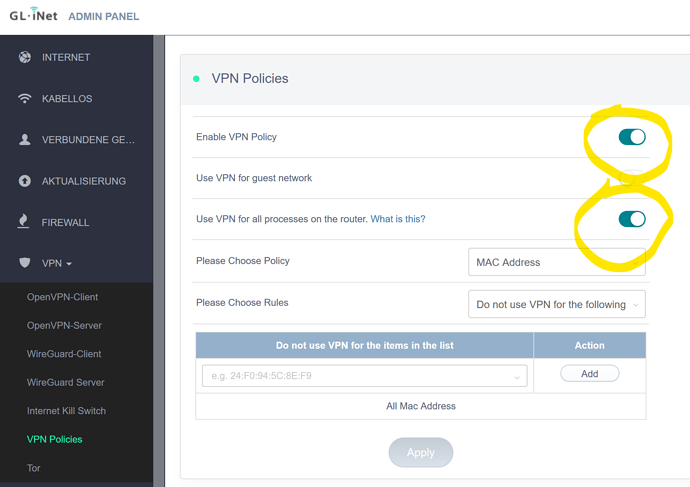
where do I turn it on… VPN policies
How do I set it!
Please with a screenshot
Hi funktion,
maybe you have to update your firmware. I’m currently running the prerelease 3.100.
In this version you can find the following in the GL.iNet Admin Panel:
Thanks @GrossmeisterBM
Unfortunately I have not yet managed to do it!
I have a GL-MT300N-V2 FirmwareV 3.102
I tried the steps from
eagle76
I was able to get this to work. This is what I did:
- Download GL-AR300M16 OpenWrt only 3.0 from https://docs.gl-inet.com/en/3/release_notes/ 50
- Update firmware
- reset to factory default
- connect to 192.168.1.1
- set password
- change IP
- enable wireless
- connect internet (modem) to WAN
Go to System-Software
- update packages
- search for vpnc
install:
- vpnc
- vpnc-scripts
- luci-proto-vpnc
System-reboot
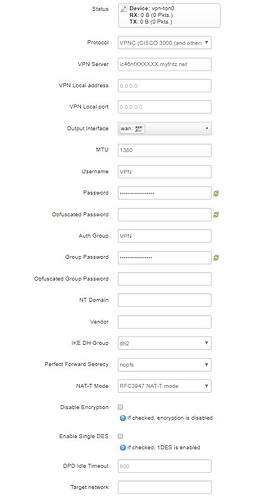
Network-interfaces: Add new interface…
name (4 charachters only! e.g. ‘TUN0’)
protocol: VPNC
VPN Server: enter url of server
Output Interafce: wan
MTU: 1380
Username: name as entered in FritzBox
Password: password for user on FritzBox
Auth Group: same as Username
Group Password: Preshared key as in FritzBox
IKE DH Group: dh2 (should be default)
Perfect Forward Secrecy: nopfs
DPD Idle Timeout: 0
Go to tab Advanced… Make sure ‘Bring up on boot’ is checked
Go to tab Firewall Settings… Assign to ‘LAN’ zone
Click ‘Save and Apply’
Network-interfaces:
Make sure TUN0 has an IP address and is up.
----------------------------------------------------------------------------------------------!
After this step, my adapter has no IP from the remote Fritzbox!
Where could my mistake be?
Does anyone have a tip?
With the Shrew Soft VPN Client it works right away!
Hey funktion,
maybe you mixed up wan and wwan as Output interface in TUN0 configuration?!
best regards
g
Moin Moin ( Hey ) grossmeisterBM
in my first attempt I only used the WAN connection and a PC on the LAN connection.
WWAN comes later as soon as I understand how the attitude is
I’m going to test other hardware because I still have a GL ar750 and a router with Open WRT directly.
Danke and best regards
Hey some information,
with a TP-1043 and a GL-AR750 I get an IP address on Tun0.
I think the routing rule is still missing or should it be done with the VPN Policies?
“try adding the following routing rules ip route add 0.0.0.0/1 dev tun ip route add 128.0.0.0/1 dev tun”
only where do I insert this line exactly?
Hello everyone,
I have the same problems as @eagle76 / @grossmeisterBM.
My system consists of a “GL.iNet GL-MT300N” and a FritzBox 7590.
The configuration is done as described by @eagle76.
The VPN tunnel is up and I got an IP address from the FritzBox.
But I have no working connection from the external LAN to the FritzBox LAN.
I guess there are also missing firewall settings.
Does anyone have new findings and can help me?
Thanks in advance!
Many greetings
Christoph
Translated with DeepL Translate: The world's most accurate translator (free version)
Hi Christoph
did you try setting the switches as described in my post from april the 17th?
Since that it workes fine for me.
Best regards
B.
Hey @grossmeisterBM,
Thanks for this information!
Of course I missed this post. ![]()
With this setting it now works for me, too.
I can now access the FritzBox-LAN from the external LAN.
But now I still have the problem that I want to access the external devices from Fritzbox-LAN, too.
Unfortunately this is not possible.
In the FritzBox I wanted to set up a static route to the external LAN, but the FB does not allow this.
Does anyone know advice?
MUCH THANKS!
Chris
(EDIT: Just realised this is a really OLD thread.)
I love my AR-300M, but for such a use I would rather look at getting another FritzBox (for example, the tiny 4020 router) and then connect both boxes using the “LAN-to-LAN linkage” option. This effectively creates a single VPN that allows remote access both to internal and to external devices at both ends.
If an AR-300M would still be required, I’d attach it to the 4020 either as an AP (tested) or in bridge mode (untested).
I have done this later configuration with two 7530s and an AR-300M, and also I’m a happy user of a network of three FritzBoxes spanning three countries connected permanently in the LAN-LAN mode. While the “route all” or “route selected LAN port” options are fairly rudimentary, the configuration works reliably.