Hello everyone,
I need assistance configuring my Brume 2 router to operate a WireGuard server in conjunction with an OpenVPN client configuration. I use the OpenVPN client to obtain a public IP from my VPN provider (PrivateVPN), as my ISP only offers CGNAT.
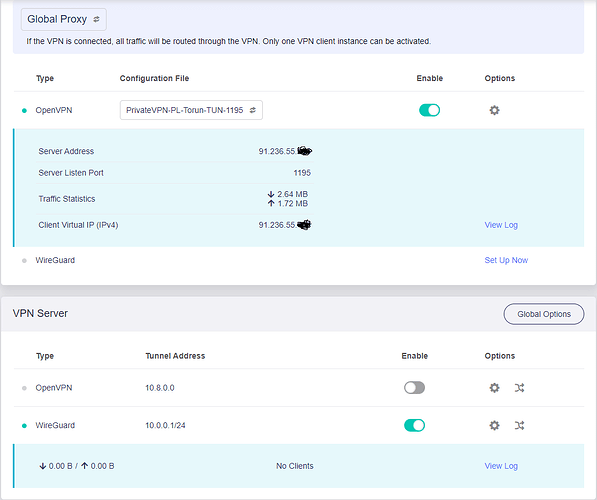
Goal: To set up a WireGuard server on the Brume 2 to allow access to my local LAN from outside.
Successes so far: I have successfully made other ports in my LAN accessible from the internet via this VPN connection by setting up port forwarding from the "OpenVPN Client" to the "LAN" zone. My VPN provider forwards the IP to me, and I can use any port I want.
Problem: Despite successful port forwarding with other services, I'm struggling to configure the WireGuard server accordingly. The default IP address for the WireGuard server on the Brume 2 is 10.0.0.1/24, and despite correct port forwarding, I cannot reach the required port.
Specific Questions:
- What specific settings and ports do I need to configure to make the WireGuard server accessible over my VPN-related public IP?
- Are adjustments needed in the zone settings (WAN, OpenVPN Client, WireGuard Server, LAN) to enable access?
I would greatly appreciate detailed advice or instructions that could help me master this setup and securely access my network from outside.
Thank you in advance for your support and advice!
Best regards,
hornet
What is the ovpn backhaul subnet IP?
You want to access the Wireguard server, through the ovpn turnnel right?
This kind of double vpn works but not ideal.
- In the opvn, you need to enable this option.
-
You need to manage the mtu of the vpn. The wireguard mtu should be lower.
-
You need to check the wireguard config, including subnet, endpoint etc to make sure they are correct.
Here is the output from the ifconfig. Just to explain, I use a static IP configuration to connect to the internet. Additionally, the LAN here is 192.168.0.1/24, and I'm looking to make it accessible from the internet via WireGuard.
thanks hornet
root@GL-MT2500:~# cd /
root@GL-MT2500:/# ifconfig
br-lan Link encap:Ethernet HWaddr 94:83:C4:2F:40:5B
inet addr:192.168.0.200 Bcast:192.168.0.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:101217 errors:0 dropped:25251 overruns:0 frame:0
TX packets:38756 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:11408584 (10.8 MiB) TX bytes:6150634 (5.8 MiB)
eth0 Link encap:Ethernet HWaddr 94:83:C4:2F:40:5A
inet addr:192.168.8.4 Bcast:192.168.8.255 Mask:255.255.255.0
inet6 addr: fe80::9683:c4ff:fe2f:405a/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:55837 errors:0 dropped:0 overruns:0 frame:0
TX packets:57644 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:5901145 (5.6 MiB) TX bytes:5423153 (5.1 MiB)
Interrupt:75
eth1 Link encap:Ethernet HWaddr 94:83:C4:2F:40:5B
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:101246 errors:0 dropped:24 overruns:0 frame:0
TX packets:40192 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:12827400 (12.2 MiB) TX bytes:6708947 (6.3 MiB)
Interrupt:75
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:882 errors:0 dropped:0 overruns:0 frame:0
TX packets:882 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:80027 (78.1 KiB) TX bytes:80027 (78.1 KiB)
ovpnclient Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:91.236.55.xxx P-t-P:91.236.55.xxx Mask:255.255.255.192
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:14349 errors:0 dropped:0 overruns:0 frame:0
TX packets:18195 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:500
RX bytes:2371039 (2.2 MiB) TX bytes:1595773 (1.5 MiB)
I see. You have a public IP in the ovpn.
So just enable the option I mentioned above and use a lower mtu (default is 1380 and hope it works fine) for wireguard and it should be OK.

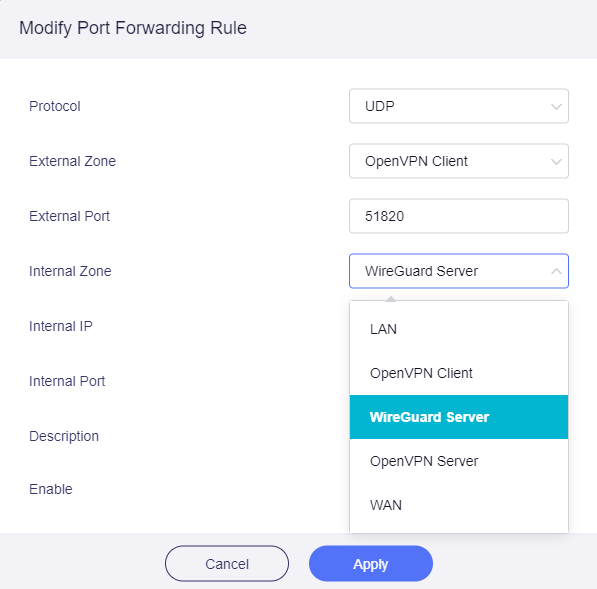
Here the settings, do I have to add portforwarding? What exact settings?
Thank you
I send you a message. I need to test.
In addition to your current base, please execute the following commands in ssh terminal
iptables -I INPUT -i ovpnclient -p udp --dport 51820 -j ACCEPT
uci set wireguard_server.main_server.fwmark='0x4000'
uci commit
ifdown wgserver
sleep 2
ifup wgserver