Hi everyone — I need some help troubleshooting a VLAN issue that started right after I updated my GL.iNet gateway.
Setup
-
Device: GL-MT2500 (hostname
GL-MT2500) running openwrt-21.02 branch (git-22.245.77575-63bfee6) / OpenWrt 21.02-SNAPSHOT. -
UniFi APs + switch for Wi-Fi. OpenWrt is the gateway (wired) and UniFi provides the SSIDs.
-
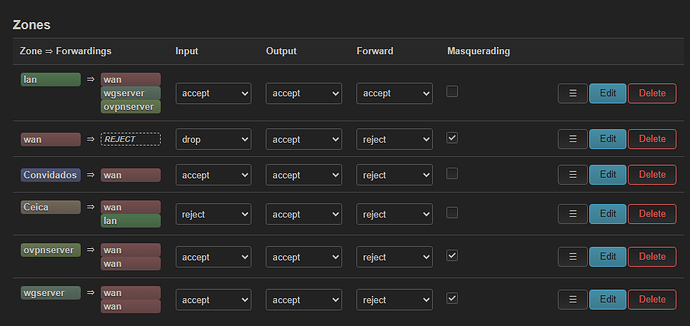
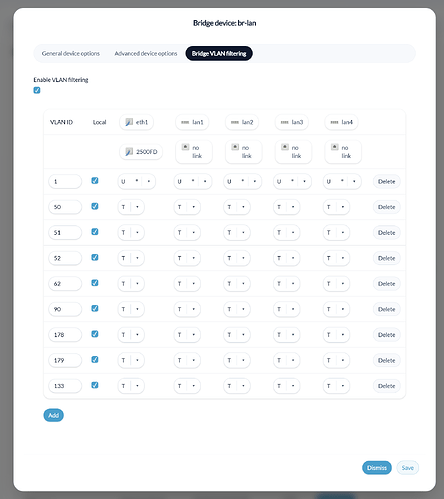
Working VLAN:
CEICA→192.168.30.1/24(VLAN id 11) — fully functional (DHCP + internet). -
Problem VLAN:
guest→192.168.9.1/24oneth1.10(VLAN id 10). Clients connect to the guest SSID, receive DHCP leases (e.g.192.168.9.x), but no Internet access (cannot reach WAN).
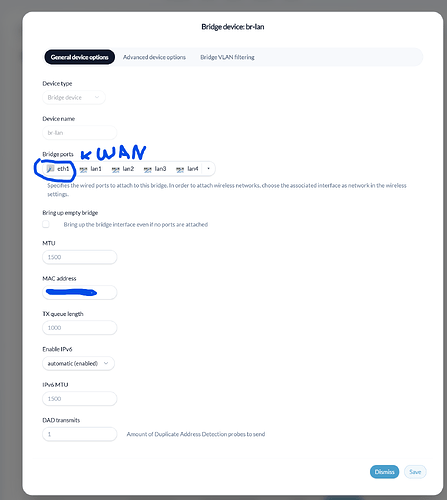
What I see in the router (LuCI)
-
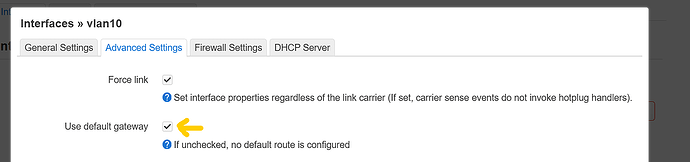
eth1.10device exists and is UP. -
Interface
guesthas static IP192.168.9.1/24. -
DHCP server for
guestis active and hands out leases (start 100, limit 150). -
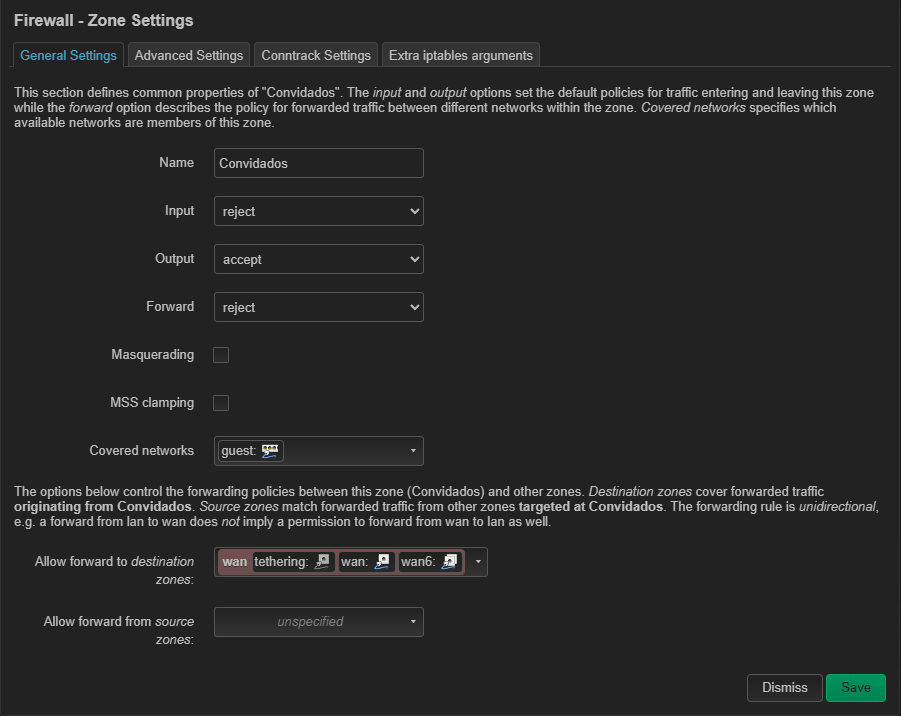
Firewall zone
guestexists, has Masquerading enabled and forward towanallowed. -
No obvious errors in System Log (no
binderrors from dnsmasq). -
I restarted
dnsmasqand reapplied the interface via LuCI — no change.
Symptoms
-
Devices on guest get IP addresses and can talk to each other / the gateway, but cannot access the WAN.
-
CEICA VLAN (192.168.30.1) works normally on the same physical uplink.
-
Problem appeared immediately after the OpenWrt update.
What I tried so far
-
Verified
eth1.10exists and shows RX/TX activity in LuCI Devices. -
Confirmed DHCP gives leases for guest.
-
Confirmed firewall zone
guesthas NAT/masquerade enabled and forward towan. -
Restarted dnsmasq / re-applied network config via LuCI.
-
Compared
guestsettings with the workingCEICAVLAN.
If anyone has seen a similar problem after upgrading to an OpenWrt 21.02 snapshot (DSA / VLAN runtime change), I’d really appreciate pointers.
Thanks in advance — I appreciate any help or ideas!