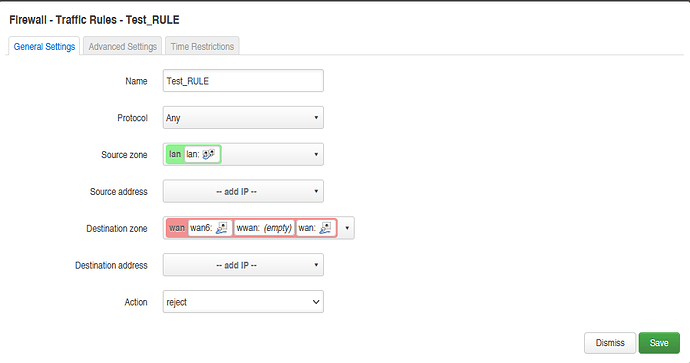
When i defining some traffic rules in the firewall even extreme rules like: Source LAN to WAN : reject all protocols have no effect - I also used different positions of the rule or rebooting the router, the rules take no effect
wireless:
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/soc/c000000.wifi'
option band '5g'
option htmode 'HE80'
option country 'US'
option disabled '0'
option channel 'auto'
option legacy_rates '0'
option channels '36 40 44 48 149 153 157 161 165'
option hwmode '11a'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option encryption 'psk2'
option wds '1'
option isolate '0'
option ssid 'WiFi_2'
option hidden '0'
option key 'XXXXXXXXXX'
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/soc/c000000.wifi+1'
option band '2g'
option country 'US'
option disabled '0'
option channel 'auto'
option htmode 'HE40'
option legacy_rates '0'
option hwmode '11g'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option encryption 'psk2'
option wds '1'
option isolate '0'
option ssid 'WiFi_5'
option hidden '0'
option key 'XXXXXXXXXX'
config wifi-iface 'guest5g'
option device 'radio0'
option network 'guest'
option mode 'ap'
option encryption 'psk2'
option ssid 'GL-AX1800-c3f-5G-Guest'
option guest '1'
option disabled '1'
option wds '1'
option isolate '1'
option key 'XXXXXXXXXX'
config wifi-iface 'guest2g'
option device 'radio1'
option network 'guest'
option mode 'ap'
option encryption 'psk2'
option ssid 'GL-AX1800-c3f-Guest'
option guest '1'
option disabled '1'
option wds '1'
option isolate '1'
option key 'XXXXXXXXXX'
network:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'xxxx:xxxx:xxxx::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
list ports 'eth2'
list ports 'eth3'
list ports 'eth4'
option multicast_to_unicast '0'
config device
option name 'eth1'
option macaddr 'xx:xx:xx:xx:xx:xx'
config device
option name 'eth2'
option macaddr 'xx:xx:xx:xx:xx:xx'
config device
option name 'eth3'
option macaddr 'xx:xx:xx:xx:xx:xx'
config device
option name 'eth4'
option macaddr 'xx:xx:xx:xx:xx:xx'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option isolate '0'
option ipaddr '10.0.1.1'
config device
option name 'eth0'
option macaddr 'xx:xx:xx:xx:xx:xx'
config interface 'wan'
option device 'eth0'
option ipv6 '0'
option proto 'static'
option ipaddr '10.0.0.1'
option gateway '10.0.0.138'
option netmask '255.255.255.0'
option peerdns '0'
option dns '1.1.1.1 1.0.0.1'
config interface 'wan6'
option device 'eth0'
option proto 'dhcpv6'
option disabled '1'
config switch
option name 'switch0'
option reset '0'
option enable_vlan '0'
config interface 'guest'
option force_link '1'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.9.1'
option netmask '255.255.255.0'
option ip6assign '60'
option multicast_querier '0'
option igmp_snooping '0'
option isolate '0'
option bridge_empty '1'
config interface 'wwan'
option proto 'dhcp'
config rule 'policy_bypass_vpn'
option mark '0x60000/0x60000'
option lookup '53'
option priority '53'
config rule 'policy_via_vpn'
option mark '0x80000/0x80000'
option lookup '52'
option priority '52'
config rule 'policy_dns'
option mark '0x100000/0x100000'
option lookup '51'
option priority '51'
config interface 'ovpnclient'
option proto 'ovpnclient'
option config '3254_7221'
option disabled '0'
dhcp:
config dnsmasq
option domainneeded '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option rebind_protection '0'
option noresolv '1'
list server '127.0.0.1#3053'
config dhcp 'lan'
option interface 'lan'
option start '100'
option leasetime '12h'
option dhcpv4 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option dhcpv6 'disabled'
option ra 'disabled'
option limit '101'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config domain
option name 'console.gl-inet.com'
option ip '10.0.1.1'
config dhcp 'guest'
option interface 'guest'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv6 'disabled'
option ra 'disabled'
firewall:
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
option output 'ACCEPT'
option forward 'REJECT'
option mtu_fix '1'
option input 'DROP'
option masq '1'
option network 'wanwan wan6 wwan wan'
config forwarding
option src 'lan'
option dest 'wan'
option enabled '0'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option target 'REJECT'
option dest 'wan'
option src 'lan'
option name 'Test_RULE'
list proto 'all'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config include 'nat6'
option path '/etc/firewall.nat6'
option reload '1'
config include 'gls2s'
option type 'script'
option path '/var/etc/gls2s.include'
option reload '1'
config include 'glblock'
option type 'script'
option path '/usr/bin/gl_block.sh'
option reload '1'
config zone
option name 'guest'
option network 'guest'
option forward 'REJECT'
option output 'ACCEPT'
option input 'REJECT'
config forwarding
option src 'guest'
option dest 'wan'
option enabled '0'
config rule
option name 'Allow-DHCP'
option src 'guest'
option target 'ACCEPT'
option proto 'udp'
option dest_port '67-68'
config rule
option name 'Allow-DNS'
option src 'guest'
option target 'ACCEPT'
option proto 'tcp udp'
option dest_port '53'
config zone 'ovpnclient'
option name 'ovpnclient'
option forward 'DROP'
option output 'ACCEPT'
option mtu_fix '1'
option network 'ovpnclient'
option enabled '1'
option input 'DROP'
option masq '1'
option masq6 '1'
config forwarding 'ovpnclient2wan'
option src 'ovpnclient'
option dest 'wan'
option enabled '1'
config forwarding 'lan2ovpnclient'
option src 'lan'
option dest 'ovpnclient'
option enabled '1'
config forwarding 'guest2ovpnclient'
option src 'guest'
option dest 'ovpnclient'
option enabled '1'
config rule 'sambasharewan'
option src 'wan'
option dest_port '137 138 139 445'
option dest_proto 'tcpudp'
option target 'DROP'
config rule 'sambasharelan'
option src 'lan'
option dest_port '137 138 139 445'
option dest_proto 'tcpudp'
option target 'ACCEPT'
config rule 'glnas_ser'
option src 'wan'
option dest_port '6000-6002'
option dest_proto 'tcp'
option target 'DROP'
config rule 'webdav_wan'
option src 'wan'
option dest_port '6008'
option dest_proto 'tcp'
option target 'DROP'
i dont know what i am doing wrong.