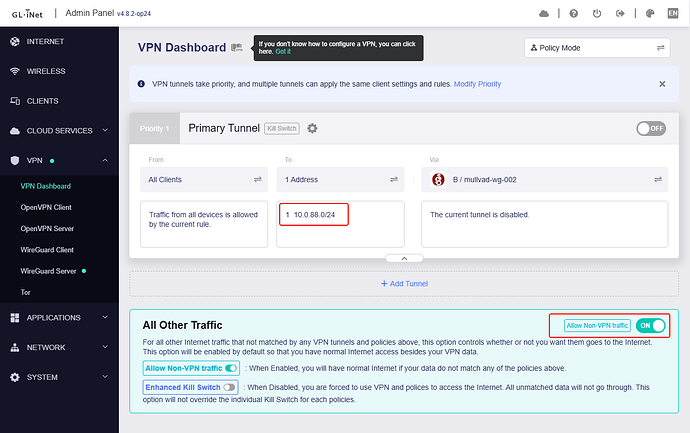
Hello GL.iNet community,
I’m currently experiencing an issue with my Flint2 router when using the WireGuard client. When the VPN connection is established, the Flint2 can access the remote VPN network (10.0.88.x), but it completely loses Internet access on the WAN side.
Here are the technical details:
Router / Firmware:
-
GL.iNet Flint2 / GL-MT6000
-
Firmware: OpenWrt 24.0 r27229+44-ebe7c5f1a3
-
Kernel Version: 6.6.47
WireGuard client configuration on Flint2:
[Interface]
Address = 10.0.88.2/32
ListenPort = 51820
PrivateKey = <hidden>
DNS = 1.1.1.1, 2606:4700:4700::1111
MTU = 1280
[Peer]
PublicKey = <server public key>
Endpoint = xx.yyy:51820
AllowedIPs = 10.0.88.0/24
PersistentKeepalive = 25
-
The Flint2 LAN IP is 10.0.0.254.
-
The VPN server is on a VPS (IONOS) with network 10.0.88.0/24.
Routing observations when VPN is active:
root@GL-MT6000:~# ip route
default via ww.xx.yy.zz dev eth1 proto static src ww.xx.yy.zz metric 10
10.0.0.0/24 dev br-lan proto kernel scope link src 10.0.0.254
ww.xx.yy.0/23 dev eth1 proto static scope link metric 10
-
I can ping and access devices on 10.0.88.x without issues.
-
Attempting to ping an external IP like 1.1.1.1 results in:
ping: sendto: Required key not available
WireGuard interface on Flint2 when active:
root@GL-MT6000:~# ip link show
...
21: wgclient: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1280 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
link/none
Server setup (VPS / IONOS):
- wg0.conf includes NAT and forwarding rules:
PostUp = sysctl -w net.ipv4.ip_forward=1
PostUp = iptables -A FORWARD -i %i -j ACCEPT
PostUp = iptables -A FORWARD -o %i -j ACCEPT
PostUp = iptables -t nat -A POSTROUTING -s 10.0.88.0/24 -o ens6 -j MASQUERADE
- AllowedIPs for the Flint2 peer is currently
10.0.88.2/32.
What I’ve tried:
-
Enabling “Access LAN” on the Flint2 WireGuard client
-
Checking
iptablesrules and routing tables -
Adjusting MTU to 1280
-
Ensuring the client WireGuard interface is up before adding routes
Observation:
-
The Flint2 successfully connects to the VPN and can reach 10.0.88.x devices.
-
However, any attempt to reach the Internet (WAN) fails, likely due to the Flint2 firmware routing all traffic through the VPN by default.
-
Setting
AllowedIPs = 0.0.0.0/0, ::/0on the client side causes server-side issues due to IPv6 default route conflicts.
Question / Request:
-
Is there a supported way to enable split tunneling on the Flint2 WireGuard client, so that only traffic destined for the VPN (10.0.88.x) goes through the tunnel, while Internet traffic continues through the WAN interface?
-
Are there recommended firewall/iptables or UCI configurations for this scenario on Flint2?
Thank you for any guidance. This behavior seems firmware-related, as the WireGuard interface itself is up and functional, but the routing prevents Internet access when the VPN is active.