Hello community and support team,
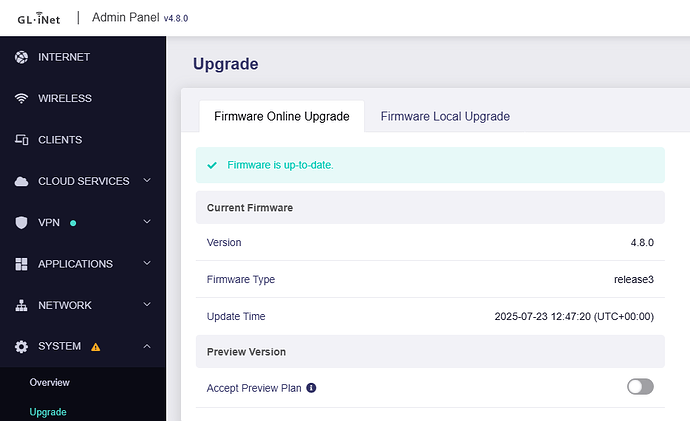
after upgrading my GL.iNet GL-MT3000 (Beryl AX) from firmware 4.7.4 release6 to 4.8 release3 via the web UI, enabling my existing WireGuard profile immediately breaks client connectivity on the router. Rolling back to 4.7.4 r6 restores normal operation.
Environment
• Device: GL-MT3000 (hardware rev unknown)
• Firmware: 4.7.4 r6 → 4.8 r3 (rollback to 4.7.4 r6 confirms resolution)
• Mode: Router
• Uplinks tested: Wi-Fi Repeater and USB tethering — issue occurs with each individually and in combination
• Clients: Wi-Fi only during tests (no wired clients)
• Home endpoint: AVM FRITZ!Box 6591 (WireGuard server, reachable over IPv6)
• Timezone: Europe/Berlin
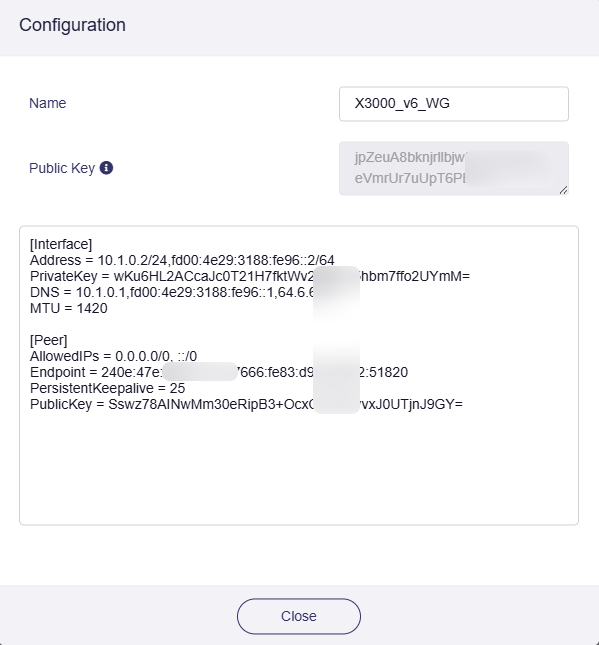
WireGuard profile (sanitized)
ini
KopierenBearbeiten
[Interface]
PrivateKey = [masked]
Address = 192.168.201.1/24
DNS = 192.168.200.1
DNS = fritz.box
[Peer]
PublicKey = [masked]
PresharedKey = [masked]
AllowedIPs = 192.168.200.0/24, 0.0.0.0/0, ::/0
Endpoint = vpnendpoint-masked.net:51463
PersistentKeepalive = 25
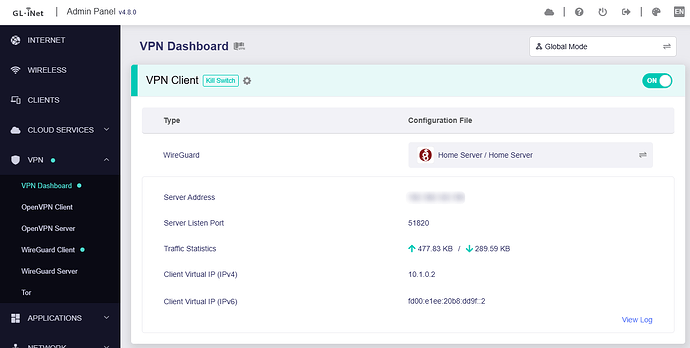
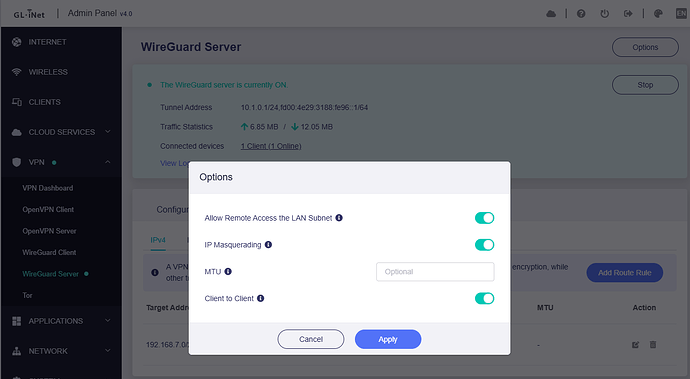
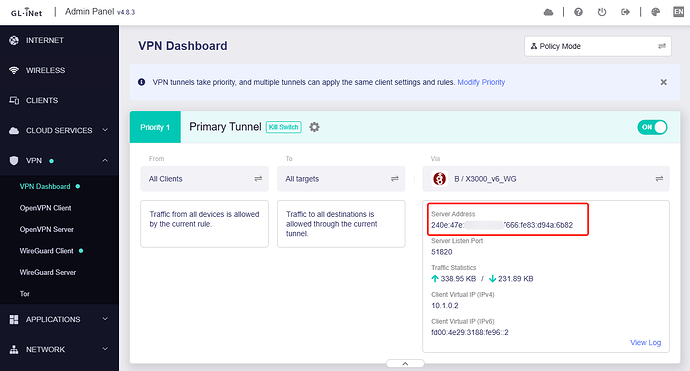
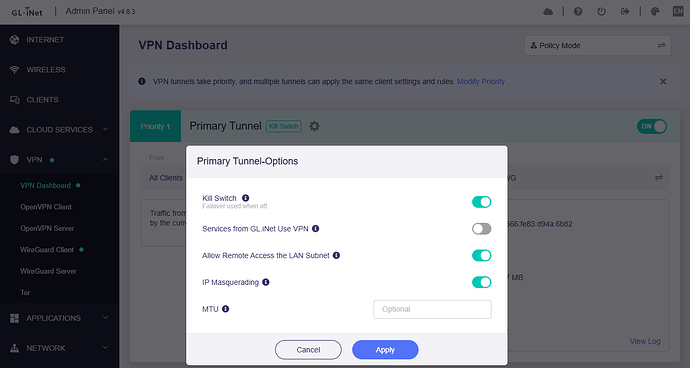
Mode: Global / route all traffic • LAN-to-LAN routing: enabled
Transport to home: IPv6, while most traffic inside the tunnel is IPv4 (plus ::/0 allowed).
Issue Summary
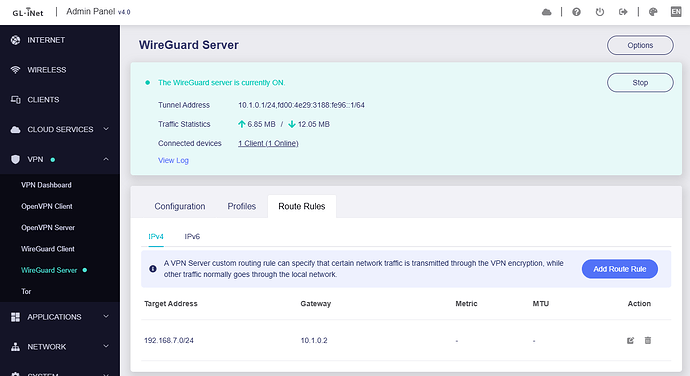
On 4.7.4 r6, clients have Internet, local LAN access, and can reach home resources over WG.
On 4.8 r3, as soon as I enable the same WG profile, Wi-Fi clients briefly disconnect/reconnect and then have no connectivity (no Internet, no access to home, no local reachability).
Meanwhile, the FRITZ!Box shows the WG tunnel as established/healthy, and from my home network I can ping the GL-MT3000 and open its web UI via the tunnel. This suggests the tunnel itself is up but client forwarding/NAT/routing on the GL-MT3000 breaks once WG is active.
Reproduction
- Upgrade GL-MT3000 from 4.7.4 r6 to 4.8 r3 via web UI.
- Connect Internet via Wi-Fi Repeater (also reproduced via USB tethering).
- Connect a client to the GL-MT3000 Wi-Fi.
- Enable the WireGuard profile (global mode; AllowedIPs as above).
→ Actual (4.8 r3): client Wi-Fi blips, then no connectivity.
→ Expected (4.7.4 r6): normal Internet/local access and working WG to home.
What I’ve Tried
• Power-cycle and factory reset on 4.8 r3, then re-apply the WG profile → issue persists.
• Policy mode instead of Global → same issue.
• USB tethering and Wi-Fi Repeater as uplinks → same issue in all cases.
• Rollback to 4.7.4 r6 → everything works again.
Regression Snapshot
• 4.7.4 r6 + WG (IPv6 transport, IPv4 routing, Global, LAN-to-LAN) → OK
• 4.8 r3 + same WG profile → Wi-Fi clients lose all connectivity upon activation
Suspected Area (for triage)
Possibly a firewall/fw4/nftables or routing/policy change in 4.8 affecting forwarding/NAT between LAN ↔ WG with IPv6 transport + IPv4 inside (0.0.0.0/0 and ::/0 AllowedIPs). Client traffic appears to be dropped/blackholed once WG is up, while the router itself remains reachable from the home side.