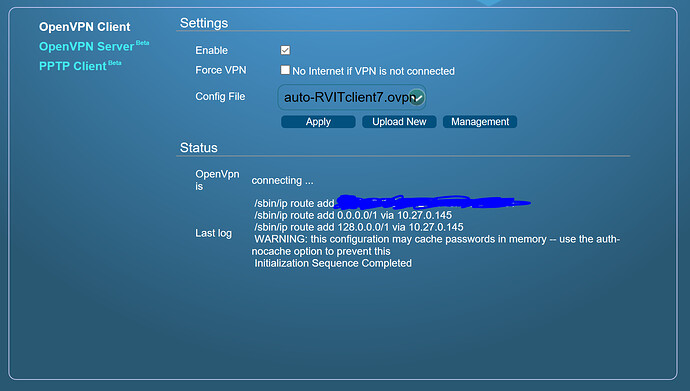
OK. I think I’ve isolated the issue. Every so often, it looks like the VPN client is attempting to reconnect. While it looks as though it fails, I think the router thinks it is connected. Here is what the status page in the GL.iNet UI looks like:
And here is the logfile showing the reconnect with connectivity down:
Sun Sep 2 13:31:22 2018 daemon.warn openvpn[1493]: WARNING: --ns-cert-type is DEPRECATED. Use --remote-cert-tls instead.
Sun Sep 2 13:31:22 2018 daemon.notice openvpn[1493]: TCP/UDP: Preserving recently used remote address: [AF_INET][Server IP Removed]
Sun Sep 2 13:31:22 2018 daemon.notice openvpn[1493]: Socket Buffers: R=[163840->200000] S=[163840->200000]
Sun Sep 2 13:31:22 2018 daemon.notice openvpn[1493]: UDP link local: (not bound)
Sun Sep 2 13:31:22 2018 daemon.notice openvpn[1493]: UDP link remote: [AF_INET][Server IP Removed]
Sun Sep 2 13:31:22 2018 daemon.notice openvpn[1493]: TLS: Initial packet from [AF_INET][Server IP Removed], sid=28f3c7fd 16395d6f
Sun Sep 2 13:31:22 2018 daemon.notice openvpn[1493]: VERIFY OK: depth=1, CN=OpenVPN CA
Sun Sep 2 13:31:22 2018 daemon.notice openvpn[1493]: VERIFY OK: nsCertType=SERVER
Sun Sep 2 13:31:22 2018 daemon.notice openvpn[1493]: VERIFY OK: depth=0, CN=OpenVPN Server
Sun Sep 2 13:31:24 2018 daemon.notice openvpn[1493]: Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Sun Sep 2 13:31:24 2018 daemon.notice openvpn[1493]: [OpenVPN Server] Peer Connection Initiated with [AF_INET][Server IP Removed]
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: Key [AF_INET][Server IP Removed] [0] not initialized (yet), dropping packet.
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: SENT CONTROL [OpenVPN Server]: ‘PUSH_REQUEST’ (status=1)
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: PUSH: Received control message: ‘PUSH_REPLY,explicit-exit-notify,topology subnet,route-delay 5 30,dhcp-pre-release,dhcp-renew,dhcp-release,route-metric 101,ping 15,ping-restart 75,comp-lzo yes,redirect-gateway def1,redirect-gateway bypass-dhcp,redirect-gateway autolocal,route-gateway 10.27.0.145,dhcp-option DNS 8.8.8.8,dhcp-option DNS 8.8.4.4,register-dns,block-ipv6,ifconfig 10.27.0.156 255.255.255.240’
Sun Sep 2 13:31:25 2018 daemon.warn openvpn[1493]: Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:4: dhcp-pre-release (2.4.3)
Sun Sep 2 13:31:25 2018 daemon.warn openvpn[1493]: Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:5: dhcp-renew (2.4.3)
Sun Sep 2 13:31:25 2018 daemon.warn openvpn[1493]: Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:6: dhcp-release (2.4.3)
Sun Sep 2 13:31:25 2018 daemon.warn openvpn[1493]: Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:17: register-dns (2.4.3)
Sun Sep 2 13:31:25 2018 daemon.warn openvpn[1493]: Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:18: block-ipv6 (2.4.3)
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: OPTIONS IMPORT: timers and/or timeouts modified
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: OPTIONS IMPORT: explicit notify parm(s) modified
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: OPTIONS IMPORT: compression parms modified
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: OPTIONS IMPORT: --ifconfig/up options modified
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: OPTIONS IMPORT: route options modified
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: OPTIONS IMPORT: route-related options modified
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: Data Channel Encrypt: Cipher ‘AES-128-CBC’ initialized with 128 bit key
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: Data Channel Encrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: Data Channel Decrypt: Cipher ‘AES-128-CBC’ initialized with 128 bit key
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: Data Channel Decrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Sun Sep 2 13:31:25 2018 daemon.notice netifd: Interface ‘VPN_client’ is enabled
Sun Sep 2 13:31:25 2018 daemon.notice netifd: Network device ‘tun0’ link is up
Sun Sep 2 13:31:25 2018 daemon.notice netifd: Interface ‘VPN_client’ has link connectivity
Sun Sep 2 13:31:25 2018 daemon.notice netifd: Interface ‘VPN_client’ is setting up now
Sun Sep 2 13:31:25 2018 daemon.notice netifd: Interface ‘VPN_client’ is now up
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: TUN/TAP device tun0 opened
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: TUN/TAP TX queue length set to 100
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: do_ifconfig, tt->did_ifconfig_ipv6_setup=0
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: /sbin/ip link set dev tun0 up mtu 1500
Sun Sep 2 13:31:25 2018 daemon.notice openvpn[1493]: /sbin/ip addr add dev tun0 10.27.0.156/28 broadcast 10.27.0.159
Sun Sep 2 13:31:25 2018 user.notice firewall: Reloading firewall due to ifup of VPN_client (tun0)
Sun Sep 2 13:31:30 2018 daemon.notice openvpn[1493]: /sbin/ip route add [Server IP Removed] via [ISP IP Removed] > Sun Sep 2 13:31:30 2018 daemon.notice openvpn[1493]: /sbin/ip route add 0.0.0.0/1 via 10.27.0.145
Sun Sep 2 13:31:30 2018 daemon.notice openvpn[1493]: /sbin/ip route add 128.0.0.0/1 via 10.27.0.145
Sun Sep 2 13:31:30 2018 daemon.warn openvpn[1493]: WARNING: this configuration may cache passwords in memory – use the auth-nocache option to prevent this
Sun Sep 2 13:31:30 2018 daemon.notice openvpn[1493]: Initialization Sequence Completed
Sun Sep 2 13:31:42 2018 daemon.info dnsmasq[2307]: read /etc/hosts - 4 addresses
Sun Sep 2 13:31:42 2018 daemon.info dnsmasq[2307]: read /tmp/hosts/dhcp.cfg02411c - 3 addresses
Sun Sep 2 13:31:42 2018 daemon.info dnsmasq-dhcp[2307]: read /etc/ethers - 0 addresses
Sun Sep 2 13:31:42 2018 daemon.warn openvpn[2905]: WARNING: --ns-cert-type is DEPRECATED. Use --remote-cert-tls instead.
Sun Sep 2 13:31:43 2018 daemon.notice openvpn[2905]: TCP/UDP: Preserving recently used remote address: [AF_INET][Server IP Removed]
Sun Sep 2 13:31:43 2018 daemon.notice openvpn[2905]: Socket Buffers: R=[163840->200000] S=[163840->200000]
Sun Sep 2 13:31:43 2018 daemon.notice openvpn[2905]: UDP link local: (not bound)
Sun Sep 2 13:31:43 2018 daemon.notice openvpn[2905]: UDP link remote: [AF_INET][Server IP Removed]
Sun Sep 2 13:31:43 2018 daemon.notice openvpn[2905]: TLS: Initial packet from [AF_INET][Server IP Removed], sid=a3898673 1c17e09e
Sun Sep 2 13:31:43 2018 daemon.notice openvpn[2905]: VERIFY OK: depth=1, CN=OpenVPN CA
Sun Sep 2 13:31:43 2018 daemon.notice openvpn[2905]: VERIFY OK: nsCertType=SERVER
Sun Sep 2 13:31:43 2018 daemon.notice openvpn[2905]: VERIFY OK: depth=0, CN=OpenVPN Server
Sun Sep 2 13:31:44 2018 daemon.notice openvpn[2905]: Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Sun Sep 2 13:31:44 2018 daemon.notice openvpn[2905]: [OpenVPN Server] Peer Connection Initiated with [AF_INET][Server IP Removed]
> Sun Sep 2 13:31:44 2018 daemon.err openvpn[1493]: Halt command was pushed by server (‘disconnected due to new connection by same user’)
> Sun Sep 2 13:31:44 2018 daemon.notice openvpn[1493]: SIGTERM received, sending exit notification to peer
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: Key [AF_INET][Server IP Removed] [0] not initialized (yet), dropping packet.
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: SENT CONTROL [OpenVPN Server]: ‘PUSH_REQUEST’ (status=1)
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: Key [AF_INET][Server IP Removed] [0] not initialized (yet), dropping packet.
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: Key [AF_INET][Server IP Removed] [0] not initialized (yet), dropping packet.
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: PUSH: Received control message: ‘PUSH_REPLY,explicit-exit-notify,topology subnet,route-delay 5 30,dhcp-pre-release,dhcp-renew,dhcp-release,route-metric 101,ping 15,ping-restart 75,comp-lzo yes,redirect-gateway def1,redirect-gateway bypass-dhcp,redirect-gateway autolocal,route-gateway 10.27.0.145,dhcp-option DNS 8.8.8.8,dhcp-option DNS 8.8.4.4,register-dns,block-ipv6,ifconfig 10.27.0.158 255.255.255.240’
Sun Sep 2 13:31:45 2018 daemon.warn openvpn[2905]: Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:4: dhcp-pre-release (2.4.3)
Sun Sep 2 13:31:45 2018 daemon.warn openvpn[2905]: Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:5: dhcp-renew (2.4.3)
Sun Sep 2 13:31:45 2018 daemon.warn openvpn[2905]: Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:6: dhcp-release (2.4.3)
Sun Sep 2 13:31:45 2018 daemon.warn openvpn[2905]: Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:17: register-dns (2.4.3)
Sun Sep 2 13:31:45 2018 daemon.warn openvpn[2905]: Unrecognized option or missing or extra parameter(s) in [PUSH-OPTIONS]:18: block-ipv6 (2.4.3)
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: OPTIONS IMPORT: timers and/or timeouts modified
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: OPTIONS IMPORT: explicit notify parm(s) modified
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: OPTIONS IMPORT: compression parms modified
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: OPTIONS IMPORT: --ifconfig/up options modified
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: OPTIONS IMPORT: route options modified
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: OPTIONS IMPORT: route-related options modified
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: Data Channel Encrypt: Cipher ‘AES-128-CBC’ initialized with 128 bit key
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: Data Channel Encrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: Data Channel Decrypt: Cipher ‘AES-128-CBC’ initialized with 128 bit key
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: Data Channel Decrypt: Using 160 bit message hash ‘SHA1’ for HMAC authentication
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: TUN/TAP device tun1 opened
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: TUN/TAP TX queue length set to 100
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: do_ifconfig, tt->did_ifconfig_ipv6_setup=0
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: /sbin/ip link set dev tun1 up mtu 1500
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[2905]: /sbin/ip addr add dev tun1 10.27.0.158/28 broadcast 10.27.0.159
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[1493]: /sbin/ip route del [Server IP Removed] > Sun Sep 2 13:31:45 2018 daemon.notice openvpn[1493]: /sbin/ip route del 0.0.0.0/1
Sun Sep 2 13:31:45 2018 daemon.notice openvpn[1493]: /sbin/ip route del 128.0.0.0/1
> Sun Sep 2 13:31:45 2018 daemon.notice openvpn[1493]: Closing TUN/TAP interface
> Sun Sep 2 13:31:45 2018 daemon.notice openvpn[1493]: /sbin/ip addr del dev tun0 10.27.0.156/28
> Sun Sep 2 13:31:45 2018 daemon.notice netifd: Network device ‘tun0’ link is down
> Sun Sep 2 13:31:45 2018 daemon.notice netifd: Interface ‘VPN_client’ has link connectivity loss
> Sun Sep 2 13:31:45 2018 daemon.notice netifd: Interface ‘VPN_client’ is now down
> Sun Sep 2 13:31:45 2018 daemon.notice openvpn[1493]: SIGTERM[soft,exit-with-notification] received, process exiting
> Sun Sep 2 13:31:45 2018 daemon.notice netifd: Interface ‘VPN_client’ is disabled
Sun Sep 2 13:31:50 2018 daemon.notice openvpn[2905]: /sbin/ip route add [Server IP Removed]via [ISP IP Removed]
Sun Sep 2 13:31:50 2018 daemon.notice openvpn[2905]: /sbin/ip route add 0.0.0.0/1 via 10.27.0.145
Sun Sep 2 13:31:50 2018 daemon.notice openvpn[2905]: /sbin/ip route add 128.0.0.0/1 via 10.27.0.145
Sun Sep 2 13:31:50 2018 daemon.warn openvpn[2905]: WARNING: this configuration may cache passwords in memory – use the auth-nocache option to prevent this
Sun Sep 2 13:31:50 2018 daemon.notice openvpn[2905]: Initialization Sequence Completed
Sun Sep 2 13:54:41 2018 daemon.info dnsmasq-dhcp[2307]: DHCPREQUEST(br-lan) 10.29.7.151 34:08:bc:3b:9c:42
Sun Sep 2 13:54:41 2018 daemon.info dnsmasq-dhcp[2307]: DHCPACK(br-lan) 10.29.7.151 34:08:bc:3b:9c:42 Hannahs-phone
Sun Sep 2 14:15:41 2018 daemon.info dnsmasq-dhcp[2307]: DHCPDISCOVER(br-lan) 10.29.7.214 24:77:03:51:0f:50
Sun Sep 2 14:15:41 2018 daemon.info dnsmasq-dhcp[2307]: DHCPOFFER(br-lan) 10.29.7.214 24:77:03:51:0f:50
Sun Sep 2 14:15:41 2018 daemon.info dnsmasq-dhcp[2307]: DHCPREQUEST(br-lan) 10.29.7.214 24:77:03:51:0f:50
Sun Sep 2 14:15:41 2018 daemon.info dnsmasq-dhcp[2307]: DHCPACK(br-lan) 10.29.7.214 24:77:03:51:0f:50 DESKTOP-605D4QH