Hello,
Recently I was having problems accessing the admin login page on my Gl-inet router, a Creta model, which is one of three models I have used in the past year or so. Out of curiosity about the coding on the login page, I opened Web inspector and found quite a few JavaScript files — one of which, I thought was a bit concerning.
To make a long story short: on October 24, 2018, I discovered that a person I went on a few dates with was accessing my computer remotely. I was a lot more naive about tech security then, which is why I was stupid enough to let them install an application on my computer called Remote Mouse a few months before…
For the last several years, I have struggled to eliminate this malware without much success, even though I’ve replaced most of my tech devices multiple times. This includes multiple routers by different companies, which is why I switched to gl-Inet in the hopes of not having to go through the same hell all over again.
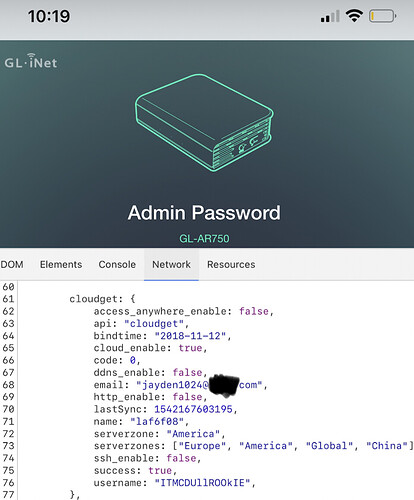
As such, I when I saw a JavaScript file in the code when I used web inspector on my router login page, I was concerned to find a few lines of code in a file called “mock.js” that included these lines of code:
cloudget: 1
access_anywhere_enable: false,
api: “cloudget”,
bindtime: “2018-11-12”,
cloud_enable: true
ddns_enable: false,
email: “jayden1024@****.com”
(Edited for brevity, see screenshot with the full code (email redacted) attached).
As my name is one that rhymes with Jayden, the date I realized I was hacked was October 24th, and the domain listed is one based in China — I was a little concerned about what I was seeing.
I sent an email to the address listed, AND received a response. The person claimed to be a former Gl-inet employee, and told me to contact support about this issue.
After emailing support, I was told that this is completely normal. That this JavaScript file, with this reference to that very specific email hosted on a Chinese mail server, is completely normal. And not to worry. That this code is present in every router that is made by Gl-inet. The support person said that this is an old code remnant used for testing, and that the use of a non-company email address was a simple mistake.
I own 2 Creta routers, and one Mango router, and found this code in all of them; however, they were all connected to my primary network a few months ago when I once again began having computer issues.
Could anyone in this forum please review the code present on their router login page for a file called “mock.js” and let me know if it is present in their router as well??
Considering that I fear my emails, tech devices, and internet connection have all been compromised, I cannot help but think this is an attempt to gaslight me for something that is NOT normal.
Any replies on this would be incredibly appreciated.
Thank you.