Since GL's development website has been down for a long time, you can access a copy of it on archive.org, where all parental-control APIs are listed in there:
GL.iNet SDK4.0 API-DOCS
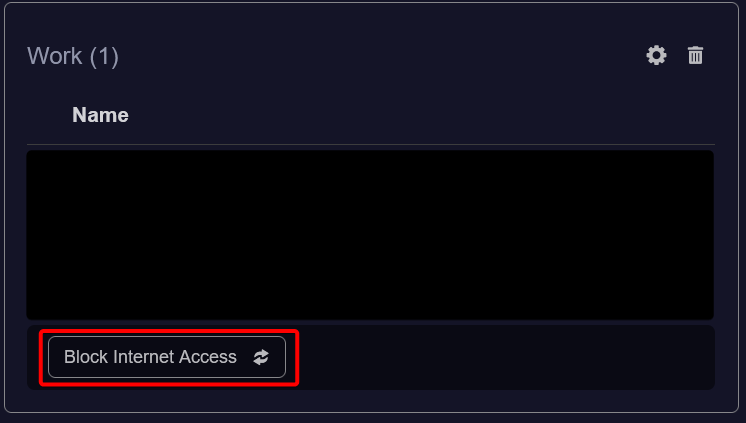
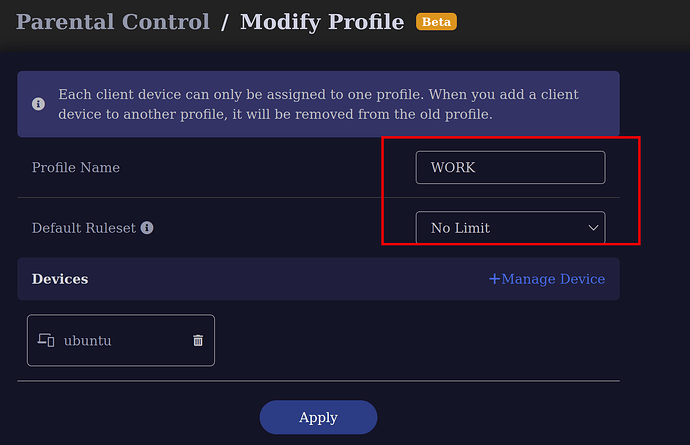
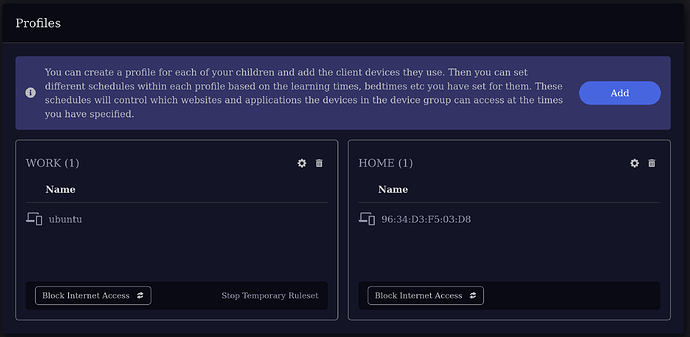
I created two different profiles on my modem as follow:
~~ EXECUTING CURL FROM ANOTHER SYSTEM ~~~
Each defined profile (e.g. WORK, HOME ...etc) within the internal system is named as groupxxxxxxx. To fetch all profiles execute this curl command after replacing the SID string below with your valid SID:
curl --path-as-is -i -s -k -X $'POST' --data-binary $'{\"jsonrpc\":\"2.0\",\"id\":11,\"method\":\"call\",\"params\":[\"9hWWULsgh3r2BktYQOqy4MKWuvJ0Ov0X\",\"parental-control\",\"get_status\",{}]}' $'https://192.168.8.1/rpc'
HTTP/1.1 200 OK
Server: nginx/1.17.7
Date: Sat, 15 Jun 2024 17:14:37 GMT
Content-Type: application/octet-stream
Transfer-Encoding: chunked
Connection: keep-alive
{"id":11,"jsonrpc":"2.0","result":{"groups":[{"id":"group2129416","rule":"drop","brief":false},{"id":"group7342748","rule":"accept","brief":false}],"time_valid":true}}
As you can see from the HTTP response above, I have two group strings: group2129416 and group7342748. These groups correspond to the WORK and HOME profiles that I defined.
Now let's say I want to ALLOW/BLOCK the internet access for my WORK profile (group7342748), I just need to set the enable key from true to false and vice versa:
curl --path-as-is -i -s -k -X $'POST' --data-binary $'{\"jsonrpc\":\"2.0\",\"id\":16,\"method\":\"call\",\"params\":[\"9hWWULsgh3r2BktYQOqy4MKWuvJ0Ov0X\",\"parental-control\",\"set_brief\",{\"enable\":true,\"manual_stop\":false,\"rule_id\":\"drop\",\"group_id\":\"group7342748\",\"time\":\"\"}]}' $'https://192.168.8.1/rpc'
HTTP/1.1 200 OK
Server: nginx/1.17.7
Date: Sat, 15 Jun 2024 17:31:57 GMT
Content-Type: application/octet-stream
Transfer-Encoding: chunked
Connection: keep-alive
{"id":16,"jsonrpc":"2.0","result":[]}
Hint! You can ping from a client added to the profile you're testing while executing the curl commands (switching true to false and vice versa) to observe how the traffic gets blocked and re-enabled again. All other useful APIs can be found in the provided link at the beginning.
~~ FROM AN SSH SESSION ~~~
Now let's say you would like to perform the same actions but after SSHing into the box. The same curl command but you do not need the Session ID (SID) string and you need to add the glinet header and finally connect to localhost:
root@GL-X3000:~# curl --path-as-is -i -s -k -X $'POST' -H $'glinet: 1' --data-binary $'{\"jsonrpc\":\"2.0\",\"id\":16,\"method\":\"call\",\"params\":[\"\",\"parental-control\",\"set_brief\",{\"enable\":false,\"manual_stop\":false,\"rule_id\":\"drop\",\"group_id\":\"group7342748\",\"time\":\"\"}]}' $'https://127.0.0.1/rpc'
HTTP/1.1 200 OK
Server: nginx/1.17.7
Date: Sat, 15 Jun 2024 17:20:46 GMT
Content-Type: application/octet-stream
Transfer-Encoding: chunked
Connection: keep-alive
{"id":16,"jsonrpc":"2.0","result":[]}