I was on the understanding that wifi 7 is effectively the 2.4ghz and 5ghz bands connected to give you 7ghz, thats kind of how its advertised, multi link operation.
For the last 3 days I've been experiencing a very weird issue. I use the Flint 3 as my upstream DNS resolver. Every day when my external IP address changes, the Flint 3's DNS server stops working and refuses to forward requests until the router is restarted. It still answers local queries but fails with "REFUSED" for anything upstream.
Hi,
Is the router used the factory power supply?
Hi,
When a DNS resolver exception occurs in Flint3, in the case where the domain name cannot be resolved, please SSH to the Flint3, and test if ping 8.8.8.8 and ping [WAN (external) gateway] are reachable?
For me, the Flint 3 MLO works well with both the Samsung S25 Ultra and the Asus TUF A14.
I also tested it during the beta phase and, apart from being a little unstable at the beginning, it has always been stable since then.
Hello,
Please let me know about this information:
Please simply draw a topology including power supply and network.
A Super Early Bird Flint 3 (f/w 4.7.11) has been setup using shipped default settings with the following additional config:
- MultiWAN - load balanced mode
- WAN1 in PPPoE mode
- WAN2 using LAN1 in PPPoE mode
- Disabled all WiFi radios
- Some wired clients have DHCP reservations
- Enabled Scheduled Reboot for once a week
- Connected consumer router via LAN port (no WAN connected) to the Flint 3 LAN port, in order to use the mesh WiFi feature (with it's own DHCP server disabled)
However, I have experienced some issues and challenges:
-
After around 27 hours working well, the router stopped providing access to the internet to all clients (wired or wireless).
Error on a wired LAN host:
Ping request could not find host google.co.uk. Please check the name and try again.
When issues like this to occur, there is no easy way to debug and determine what went wrong and why.
Please may I request a GL.iNet diagnostics page on the interface to help understand what caused the issue and allow any relevant failure logs to be captured (with automatic redaction of sensitive data) and allow easy reporting to GL.iNet support?Also, having an option in GL.iNet interface to auto detect no internet access on router through pings at intervals, then restart specific interfaces, if that still fails, reboot router?
-
For incoming services (port 80, 443, etc) from MultiWAN, I have port forwarded to WAN zone for each port. However, with MultiWAN in load balanced mode, it has two WAN addresses it can forward from and I'm assuming it intermittently switches between them.
The issue is that I need to 'force route' one IP to only one of the WANs, let's say "WAN1".
There is no configuration available that allows incoming/outgoing connections policy to force the WAN route by IP, so I think it constantly keeps switching between two IPs and the service Dynamic DNS can't handle the constant switching from IP1 to IP2.
Please may I request a feature to bring this MultiWAN route incoming/outgoing configuration policy into the interface? -
The router seems to be running on the boundary of HOT all the time, 70-75 deg C.
I have checked 'top' (see below), and there doesn't seem to be processes using significant CPU time, and note, all my WiFi radios are turned off, so they cannot be the source of the problem.
What other diagnostics could I employ use to determine the source of high temperature?
Mem: 399172K used, 483920K free, 2328K shrd, 22184K buff, 51556K cached
CPU: 0% usr 1% sys 0% nic 96% idle 0% io 0% irq 0% sirq
Load average: 1.04 1.11 1.14 3/181 30658
PID PPID USER STAT VSZ %VSZ CPU %CPU COMMAND
17908 1 root S 13840 2% 3 0% /usr/bin/lua /usr/bin/gl_clients_update
1 0 root S 1976 0% 1 0% /sbin/procd
17283 1 root S 1956 0% 1 0% {gl_led} /bin/sh /usr/bin/gl_led
17717 6228 root S 1156 0% 0 0% /usr/sbin/dropbear -F -P /var/run/dropbear.1.pid -p 22 -K 300 -T 3 -W
35 2 root IW 0 0% 3 0% [kworker/3:1-mm_]
29482 18517 root R 1496 0% 3 0% top
18526 17717 root S 1460 0% 0 0% ash -c while true; do sleep 1;head -v -n 8 /proc/meminfo; head -v -n
681 1 ubus S 1400 0% 0 0% /sbin/ubusd
149 2 root IW 0 0% 1 0% [kworker/1:2-mm_]
15 2 root SW 0 0% 1 0% [ksoftirqd/1]
14582 14396 root S 17600 2% 0 0% nginx: worker process
14583 14396 root S 17152 2% 3 0% nginx: worker process
14584 14396 root S 16956 2% 2 0% nginx: worker process
14585 14396 root S 16848 2% 0 0% nginx: worker process
7149 1 root S 11624 1% 1 0% hostapd -g /var/run/hostapd/global -B -P /var/run/hostapd-global.pid
7199 1 root S 11620 1% 1 0% wpa_supplicant -g /var/run/wpa_supplicantglobal -B -P /var/run/wpa_su
14396 1 root S 11176 1% 1 0% nginx: master process /usr/sbin/nginx -c /etc/nginx/nginx.conf -g dae
16578 1 root S 8188 1% 2 0% /usr/bin/sms_manager
9769 1 root S 8096 1% 2 0% /usr/sbin/uhttpd -f -h /www -r GL-BE9300 -x /cgi-bin -u /ubus -t 60 -
1359 1 root S 5432 1% 1 0% eco /usr/sbin/gl-ngx-session
22556 22554 dnsmasq S 5020 1% 1 0% /usr/sbin/dnsmasq -C /var/etc/dnsmasq.conf.cfg01411c -k -x /var/run/d
22566 22556 root S 4860 1% 2 0% /usr/sbin/dnsmasq -C /var/etc/dnsmasq.conf.cfg01411c -k -x /var/run/d
5798 1 root S 4824 1% 3 0% /usr/bin/eco /usr/sbin/gl-repeater
949 1 root S 4056 0% 1 0% /usr/bin/cnssdaemon -s
5475 1 root S 3852 0% 0 0% /sbin/rpcd -s /var/run/ubus/ubus.sock -t 30
17773 1 root S 3712 0% 3 0% /usr/bin/eco /usr/bin/alarm_event_report
5748 1 root S 3056 0% 1 0% /usr/bin/lua /usr/sbin/qca-wifi-configurator
17642 1 root S 2776 0% 3 0% {ntpd} /sbin/ujail -t 5 -n ntpd -U ntp -G ntp -C /etc/capabilities/nt
22554 1 root S 2776 0% 1 0% {dnsmasq} /sbin/ujail -t 5 -n dnsmasq -u -l -r /bin/ubus -r /etc/TZ -
10390 1 nobody S 2624 0% 1 0% avahi-daemon: running [GL-BE9300.local]
6529 1 root S 2156 0% 3 0% /sbin/netifd
9959 1 root S 1956 0% 3 0% /usr/bin/dbus-daemon --system --nofork
1395 1 root S 1852 0% 0 0% /usr/sbin/acfg_tool -e -s -t 192.168.1.2
18517 17717 root S 1468 0% 3 0% -ash
-
Using the GL.iNet interface, the Dynamic DNS should be available for MultiWAN setups and custom DNS providers such as DuckDNS, FreeDNS, and others?
-
Network Acceleration is enabled by default, but causes issues with services Port Forwarded on ports 80/443 to 192.168.8.52. When Network Acceleration is disabled, these external services start to work immediately and load is typically below 0.5. When re-enabled, these external services stop working and load is above 1.0.
From config page info: "Network acceleration reduces CPU load and speeds up traffic packet forwarding, but can conflict with some features."
It seems there are some serious issues with Network Acceleration implementation that causes strange router behaviors for port forwarding and high avg CPU load (see top below), which is opposite to the info message above?
Mem: 429940K used, 453152K free, 3652K shrd, 30056K buff, 76820K cached
CPU: 3% usr 4% sys 0% nic 90% idle 0% io 0% irq 1% sirq
Load average: 0.30 0.33 0.41 2/174 23837
PID PPID USER STAT VSZ %VSZ CPU %CPU COMMAND
17908 1 root S 13876 2% 1 0% /usr/bin/lua /usr/bin/gl_clients_update
1 0 root S 1996 0% 0 0% /sbin/procd
5475 1 root S 3868 0% 0 0% /sbin/rpcd -s /var/run/ubus/ubus.sock -t 30
681 1 ubus S 1400 0% 1 0% /sbin/ubusd
17717 6228 root S 1156 0% 1 0% /usr/sbin/dropbear -F -P /var/run/dropbear.1.pid -p 22 -K 300 -T 3 -W
9769 1 root S 8224 1% 1 0% /usr/sbin/uhttpd -f -h /www -r GL-BE9300 -x /cgi-bin -u /ubus -t 60 -
22556 22554 dnsmasq S 5028 1% 0 0% /usr/sbin/dnsmasq -C /var/etc/dnsmasq.conf.cfg01411c -k -x /var/run/d
6529 1 root S 2156 0% 2 0% /sbin/netifd
23356 18517 root R 1496 0% 0 0% top
18526 17717 root S 1460 0% 1 0% ash -c while true; do sleep 1;head -v -n 8 /proc/meminfo; head -v -n
35 2 root IW 0 0% 3 0% [kworker/3:1-mm_]
153 2 root IW 0 0% 0 0% [kworker/0:2-eve]
14585 14396 root S 19456 2% 0 0% nginx: worker process
14584 14396 root S 18620 2% 1 0% nginx: worker process
14583 14396 root S 18440 2% 3 0% nginx: worker process
14582 14396 root S 17752 2% 2 0% nginx: worker process
7149 1 root S 11624 1% 3 0% hostapd -g /var/run/hostapd/global -B -P /var/run/hostapd-global.pid
7199 1 root S 11620 1% 1 0% wpa_supplicant -g /var/run/wpa_supplicantglobal -B -P /var/run/wpa_su
14396 1 root S 11176 1% 1 0% nginx: master process /usr/sbin/nginx -c /etc/nginx/nginx.conf -g dae
16578 1 root S 8188 1% 0 0% /usr/bin/sms_manager
1359 1 root S 5456 1% 3 0% eco /usr/sbin/gl-ngx-session
22566 22556 root S 4860 1% 2 0% /usr/sbin/dnsmasq -C /var/etc/dnsmasq.conf.cfg01411c -k -x /var/run/d
5798 1 root S 4824 1% 1 0% /usr/bin/eco /usr/sbin/gl-repeater
949 1 root S 4056 0% 1 0% /usr/bin/cnssdaemon -s
17773 1 root S 3712 0% 2 0% /usr/bin/eco /usr/bin/alarm_event_report
5748 1 root S 3056 0% 1 0% /usr/bin/lua /usr/sbin/qca-wifi-configurator
17642 1 root S 2776 0% 3 0% {ntpd} /sbin/ujail -t 5 -n ntpd -U ntp -G ntp -C /etc/capabilities/nt
22554 1 root S 2776 0% 1 0% {dnsmasq} /sbin/ujail -t 5 -n dnsmasq -u -l -r /bin/ubus -r /etc/TZ -
10390 1 nobody S 2620 0% 2 0% avahi-daemon: running [GL-BE9300.local]
17283 1 root S 1956 0% 2 0% {gl_led} /bin/sh /usr/bin/gl_led
9959 1 root S 1956 0% 3 0% /usr/bin/dbus-daemon --system --nofork
1395 1 root S 1852 0% 0 0% /usr/sbin/acfg_tool -e -s -t 192.168.1.2
18517 17717 root S 1468 0% 3 0% -ash
9551 1 root S 1460 0% 0 0% /usr/sbin/crond -f -c /tmp/gl_crontabs -l 10
-
For the status page, it would be great to see more than 3 minutes of plotted data. Maybe a GL.iNet interface option to change this graph interval to 5, 10, 30, 60 minutes?
-
There is no way to backup or restore the current full configuration of the router using the GL.iNet interface. It would be ideal to have this feature with options to save them to router or local device?
Got my new Flint 3 was a little concerned about the Wi-Fi coverage reading other comments, but I check the 2.5Ghz & 5.8GHz and as far as I'm concerned the coverage is the same as the Flint 2.
Now the bad news Like the beta firmware's for the Slate AX and the Flint 1 the Flint 3 firmware 4.711 fail to update AdGuard correctly, so until its sorted out i am sticking with my Flint 2 on firmware 4.7.7 and the Firmware 4.6.11 on the Slate AX.
I don't understand what has been changed to effect the upgrade of AdGuard Home so badly.
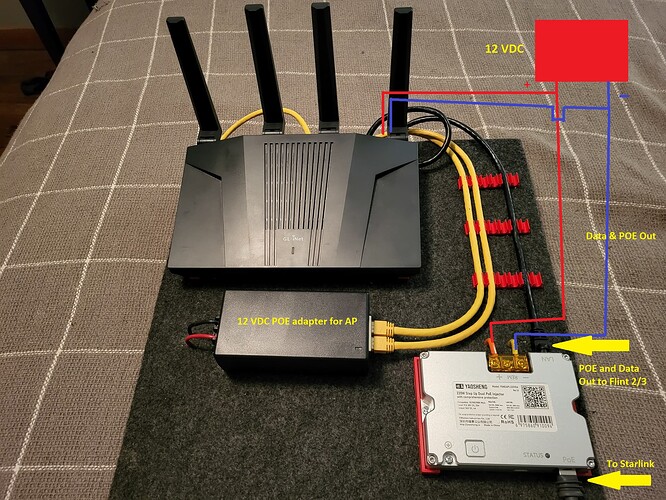
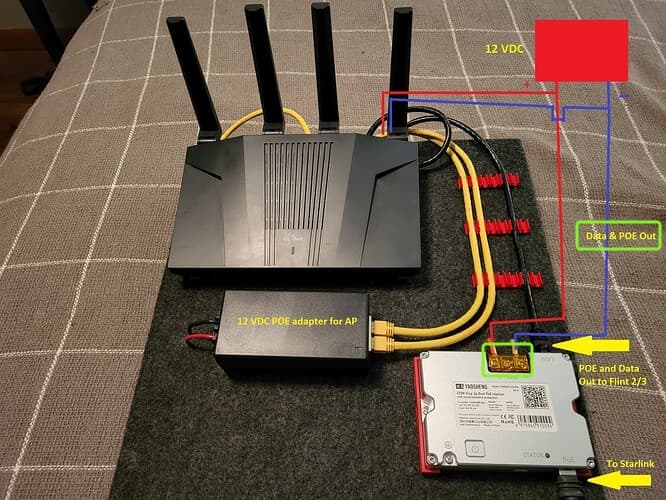
- Yes that is the Yaosheng
- Correct, the Yaosheng and Flint routers run from 12 vdc straight from a battery.
- Yes Yao provides POE power to the SL dish and ALSO outputs POE & Data to flint 3.
- Flint 3 power is straight from a 12 vdc battery bank through a barrel connector. If I use the 120 VAC included power adapter the Flint 3 start normal and adaptes show no faults.
- Yes Flint 3 works perfect when not hooked up to yaosheng or EDUP adapters.
- NO, as soon as the Flint 3 12 vdc power applied the adapters fault out.
- yes
The problem happens when power is turned on the flint 3. With the cable connected to Yaosheng/EDUP the adapters show no faults with power off the flint 3. As soon as power is turned on the flint 3 both adapters with show short circuit.
Both Adapters I have tried have a POE and Data output to the flint 3 when running on the same 12vdc source. Both Adapters work perfect with Flint 2.
Thinking maybe Flint 3 does not like a poe input on wan powered from the same source as the adapter, but Flint 2 works PERFECT with both adapters from the same 12vdc source.
Thank you for your suggestions on points 1, 2, 4, 6, and 7. We have recorded them and fed them back to our team.
For point 3, I don't have a good way to help you check the source of the temperature. And turning off the SSID does not completely turn off the radio. You can check the status of the wireless interface through the ifconfig and iw dev commands.
For point 5, turning on hard acceleration will affect the wired port forwarding rules.
I completely agree. Updating AdGuardHome using --update appears to work at first, but afterwards AdGuardHome stops functioning. Manually replacing the binary via WinSCP doesn't solve the issue either. There is definitely something wrong with how AdGuardHome works on the Flint 3.
How can I set up and configure sqm/qos for a bunch of clients?
Thanks for your updates, very clear!
Here probably is key point, the Yaosheng/EDUP (LAN, Ethernet) to Flint 2/3 is including the PoE and Data:
-
Is there a way to isolate PoE (power), only data is retained?
Since whether it is Flint2 or 3, all their WAN/LAN ports do not support PoE (PD). -
Is Yaosheng/EDUP (LAN, Ethernet) PoE standard protocol 802.11at or 802.11af?
In theory, if Flint2/3 does not accept PoE (PD), Yaosheng/EDUP (PSE, LAN Ethernet) should not be provided PoE (power), and only Data. -
There is another place that needs to be clarified.
Is the green part in the diagram below the power input of the Yaosheng module? (Not Data & PoE out)
-
This information is very important, which means the issue has nothing to do the side of SL PoE, but the side of Yaosheng+Flint3. Thank you very very much.
After Point 3 is clarified, I collate this information with the development team for review.
Hi,
GL GUI does not support batch set the limit speed of clients for the time being, but separately for each client.
The plugin SQM QoS seems to only support set limit speed for the specified interface.
So at the moment there is no solution to priorize different clients? Cake or better cake with priorizing?
Exactly mine worked for about 20 minutes and stoped, it’s been a problem for ages on the other routers i mentioned Flint 2 is the only router with no problems, beta firmware’s are no good either. The only answer is to stay on the firmware before the problem, but the Flint 3 is unusable at present.
I use the script to update AdGuard and it works perfectly.
AdGuard updated from v0.107.62 to v0.107.63 and continues to work, I updated the firmware from 4.7.11 to 4.7.13 and it continues to work, I restarted the router several times for further testing and the updated AdGuard always worked perfectly.
Same thing on Slate 7
I have setup my BE9300 as an access point to replace my old AmplifiHD. But on our MacBook Air (MacOS26), Samsung S24U, iPhone SE2020, iPhone 13ProMax we experience sometimes connection loss. The only way back is to reconnect the wifi by selecting one of the BE9300 access points again. 5G/6G/MLO (not using the 2.4). My travel router Slate7 never has this issue. Not with looking at the old AmplifiHD or now looking to the BE9300.
Samsung S24U is running latest OneUI7
iPhone SE2020 is running iOS26
iPhone Pro Max 13 is running iOS18.5
Slate7 is connected thru wifi to the Flint3, not hard wired.
Thanks for the reply are you talking about the script by admon, as I’ve never tried that I’ve always used WinSCP don’t understand why that should fail on recent firmware’s been using it for ages