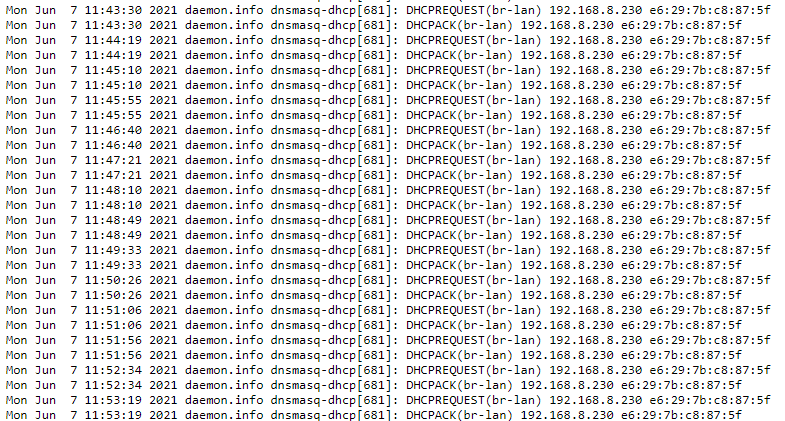
I have a GL-MT1300 running a WireGuard client. It is connected to either a wireless AP, LAN or USB tethering. With any of the three WAN connections the LAN devices will regularly disconnect from the GL-MT1300’s wireless network. It seems like the Wireless network goes down about every 5 minutes for 20 seconds or so.
When I factor reset it stops happening for a day or two and then continues to happen.
This happens with both 2.4GHz and 5GHz with WPA2 and WPA3. I’m running the
3.201 firmware but it also happened with the previous firmware version.
Besides the wireless LAN options, WireGuard client, DNS rebinding and DNS over TLS I haven’t made any changes to the default settings.
As a new user I can’t attach the kernel log (uploads and copying it don’t work). The last few lines look like this though
[ 1086.342182] WextMboSendStaDisassocToDaemonEvent [18:cf:5e:fc:75:d3] sizeof 6 report_buf_len 6 buflen 180 msg_type MBO_MSG_REMOVE_STA
[ 1091.208615] AP SETKEYS DONE - AKMMap=WPA2PSK, PairwiseCipher=AES, GroupCipher=AES, wcid=1 from 18:CF:5E:FC:75:D3
[ 1091.208615]
[ 1123.336262] scan_ch_restore,central ch=42,bw=2
[ 1123.336262]
[ 1127.111874] scan_ch_restore,central ch=1,bw=0
[ 1127.111874]
[ 1131.380779] WextMboSendStaDisassocToDaemonEvent [18:cf:5e:fc:75:d3] sizeof 6 report_buf_len 6 buflen 180 msg_type MBO_MSG_REMOVE_STA
[ 1135.305474] AP SETKEYS DONE - AKMMap=WPA2PSK, PairwiseCipher=AES, GroupCipher=AES, wcid=1 from 18:CF:5E:FC:75:D3
[ 1135.305474]
[ 1168.461950] scan_ch_restore,central ch=42,bw=2
[ 1168.461950]
[ 1172.250745] scan_ch_restore,central ch=1,bw=0
[ 1172.250745]
[ 1176.339458] WextMboSendStaDisassocToDaemonEvent [18:cf:5e:fc:75:d3] sizeof 6 report_buf_len 6 buflen 180 msg_type MBO_MSG_REMOVE_STA
[ 1180.265164] AP SETKEYS DONE - AKMMap=WPA2PSK, PairwiseCipher=AES, GroupCipher=AES, wcid=1 from 18:CF:5E:FC:75:D3
[ 1180.265164]
[ 1213.613628] scan_ch_restore,central ch=42,bw=2
[ 1213.613628]
[ 1217.389299] scan_ch_restore,central ch=1,bw=0
[ 1217.389299]
[ 1221.218199] WextMboSendStaDisassocToDaemonEvent [18:cf:5e:fc:75:d3] sizeof 6 report_buf_len 6 buflen 180 msg_type MBO_MSG_REMOVE_STA
[ 1226.066962] AP SETKEYS DONE - AKMMap=WPA2PSK, PairwiseCipher=AES, GroupCipher=AES, wcid=1 from 18:CF:5E:FC:75:D3
[ 1226.066962]
[ 1258.076862] scan_ch_restore,central ch=42,bw=2
[ 1258.076862]
[ 1261.750377] WextMboSendStaDisassocToDaemonEvent [18:cf:5e:fc:75:d3] sizeof 6 report_buf_len 6 buflen 180 msg_type MBO_MSG_REMOVE_STA
[ 1262.399097] scan_ch_restore,central ch=1,bw=0
[ 1262.399097]
[ 1262.982267] AP SETKEYS DONE - AKMMap=WPA2PSK, PairwiseCipher=AES, GroupCipher=AES, wcid=1 from 18:CF:5E:FC:75:D3
[ 1262.982267]
[ 1303.790992] scan_ch_restore,central ch=42,bw=2
[ 1303.790992]
[ 1306.175549] WextMboSendStaDisassocToDaemonEvent [18:cf:5e:fc:75:d3] sizeof 6 report_buf_len 6 buflen 180 msg_type MBO_MSG_REMOVE_STA
[ 1310.210210] AP SETKEYS DONE - AKMMap=WPA2PSK, PairwiseCipher=AES, GroupCipher=AES, wcid=1 from 18:CF:5E:FC:75:D3
[ 1310.210210]