I initially had my DNS configured in the Network > DNS section. Then, I enabled AdGuard instead. In both instances, directly connected (via Ethernet) PCs had no problems accessing the Internet (and that’s still the case).
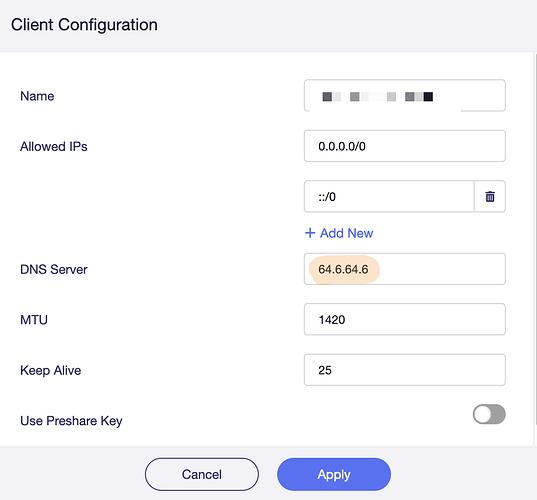
Additionally, when Wireguard VPN profiles are created, there is an option to set the DNS. If you don’t set this to anything different, the Brume 2 automatically sets it to what you see in this screenshot:
I am able to establish connections to the VPN server. These are logs from connecting this morning:
2023-02-25 07:14:22.562182: [APP] startActivation: Entering (tunnel: Brume 2)
2023-02-25 07:14:22.569597: [APP] startActivation: Starting tunnel
2023-02-25 07:14:22.570165: [APP] startActivation: Success
2023-02-25 07:14:22.587532: [APP] Tunnel 'Brume 2' connection status changed to 'connecting'
2023-02-25 07:14:22.767197: [NET] App version: 1.0.16 (27)
2023-02-25 07:14:22.770575: [NET] Starting tunnel from the app
2023-02-25 07:14:23.029882: [NET] DNS64: mapped <My Home IPv4 Address> to itself.
2023-02-25 07:14:23.030584: [NET] Attaching to interface
2023-02-25 07:14:23.030933: [NET] Routine: encryption worker 1 - started
2023-02-25 07:14:23.030994: [NET] UAPI: Updating private key
2023-02-25 07:14:23.031028: [NET] Routine: encryption worker 5 - started
2023-02-25 07:14:23.031040: [NET] Routine: encryption worker 6 - started
2023-02-25 07:14:23.031048: [NET] Routine: handshake worker 2 - started
2023-02-25 07:14:23.031093: [NET] Routine: encryption worker 3 - started
2023-02-25 07:14:23.031094: [NET] Routine: decryption worker 5 - started
2023-02-25 07:14:23.031136: [NET] Routine: decryption worker 3 - started
2023-02-25 07:14:23.031164: [NET] Routine: decryption worker 4 - started
2023-02-25 07:14:23.031198: [NET] Routine: handshake worker 5 - started
2023-02-25 07:14:23.031204: [NET] Routine: handshake worker 4 - started
2023-02-25 07:14:23.031135: [NET] Routine: encryption worker 4 - started
2023-02-25 07:14:23.031226: [NET] Routine: handshake worker 6 - started
2023-02-25 07:14:23.031232: [NET] UAPI: Updating listen port
2023-02-25 07:14:23.031244: [NET] Routine: decryption worker 1 - started
2023-02-25 07:14:23.031246: [NET] Routine: TUN reader - started
2023-02-25 07:14:23.031255: [NET] Routine: handshake worker 3 - started
2023-02-25 07:14:23.031285: [NET] Routine: decryption worker 6 - started
2023-02-25 07:14:23.031342: [NET] Routine: encryption worker 2 - started
2023-02-25 07:14:23.031347: [NET] Routine: decryption worker 2 - started
2023-02-25 07:14:23.031379: [NET] Routine: event worker - started
2023-02-25 07:14:23.031384: [NET] UAPI: Removing all peers
2023-02-25 07:14:23.031384: [NET] Routine: handshake worker 1 - started
2023-02-25 07:14:23.031732: [NET] peer(zxCt…SZTk) - UAPI: Created
2023-02-25 07:14:23.031774: [NET] peer(zxCt…SZTk) - UAPI: Updating endpoint
2023-02-25 07:14:23.031825: [NET] peer(zxCt…SZTk) - UAPI: Updating persistent keepalive interval
2023-02-25 07:14:23.031864: [NET] peer(zxCt…SZTk) - UAPI: Removing all allowedips
2023-02-25 07:14:23.031906: [NET] peer(zxCt…SZTk) - UAPI: Adding allowedip
2023-02-25 07:14:23.031992: [NET] peer(zxCt…SZTk) - UAPI: Adding allowedip
2023-02-25 07:14:23.032353: [NET] UDP bind has been updated
2023-02-25 07:14:23.032388: [NET] peer(zxCt…SZTk) - Starting
2023-02-25 07:14:23.032411: [NET] Routine: receive incoming v4 - started
2023-02-25 07:14:23.032414: [NET] Routine: receive incoming v6 - started
2023-02-25 07:14:23.032449: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:14:23.032510: [NET] peer(zxCt…SZTk) - Sending handshake initiation
2023-02-25 07:14:23.032679: [NET] peer(zxCt…SZTk) - Routine: sequential sender - started
2023-02-25 07:14:23.032689: [NET] peer(zxCt…SZTk) - Routine: sequential receiver - started
2023-02-25 07:14:23.033321: [NET] Interface state was Down, requested Up, now Up
2023-02-25 07:14:23.033352: [NET] Device started
2023-02-25 07:14:23.033440: [NET] Tunnel interface is utun7
2023-02-25 07:14:23.034589: [APP] Tunnel 'Brume 2' connection status changed to 'connected'
2023-02-25 07:14:23.035517: [NET] Network change detected with satisfied route and interface order [en0, pdp_ip0]
2023-02-25 07:14:23.035762: [NET] DNS64: mapped <My Home IPv4 Address> to itself.
2023-02-25 07:14:23.035837: [NET] peer(zxCt…SZTk) - UAPI: Updating endpoint
2023-02-25 07:14:23.036011: [NET] Routine: receive incoming v4 - stopped
2023-02-25 07:14:23.036067: [NET] Routine: receive incoming v6 - stopped
2023-02-25 07:14:23.036263: [NET] UDP bind has been updated
2023-02-25 07:14:23.036275: [NET] Routine: receive incoming v4 - started
2023-02-25 07:14:23.036291: [NET] Routine: receive incoming v6 - started
2023-02-25 07:14:23.047289: [NET] peer(zxCt…SZTk) - Received handshake response
2023-02-25 07:14:23.052198: [NET] Network change detected with satisfied route and interface order [en0, utun7, pdp_ip0]
2023-02-25 07:14:23.052448: [NET] DNS64: mapped <My Home IPv4 Address> to itself.
2023-02-25 07:14:23.052544: [NET] peer(zxCt…SZTk) - UAPI: Updating endpoint
2023-02-25 07:14:23.052708: [NET] Routine: receive incoming v4 - stopped
2023-02-25 07:14:23.052739: [NET] Routine: receive incoming v6 - stopped
2023-02-25 07:14:23.052956: [NET] UDP bind has been updated
2023-02-25 07:14:23.052992: [NET] Routine: receive incoming v4 - started
2023-02-25 07:14:23.053014: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:14:23.053039: [NET] Routine: receive incoming v6 - started
2023-02-25 07:14:23.060478: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:14:27.570035: [APP] Status update notification timeout for tunnel 'Brume 2'. Tunnel status is now 'connected'.
2023-02-25 07:14:33.267674: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:15:15.915267: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:15:30.217048: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:15:43.064113: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:16:00.577640: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:16:23.101893: [NET] peer(zxCt…SZTk) - Sending handshake initiation
2023-02-25 07:16:23.120459: [NET] peer(zxCt…SZTk) - Received handshake response
2023-02-25 07:16:23.120628: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:16:51.624165: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:17:17.600786: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:17:43.984737: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:18:10.979312: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:18:37.698108: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:19:03.704879: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:19:30.410083: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:19:30.410207: [NET] peer(zxCt…SZTk) - Sending handshake initiation
2023-02-25 07:19:30.410305: [NET] peer(zxCt…SZTk) - Received handshake initiation
2023-02-25 07:19:30.411244: [NET] peer(zxCt…SZTk) - Sending handshake response
2023-02-25 07:19:30.411366: [NET] peer(zxCt…SZTk) - Failed to create response message: handshake initiation must be consumed first
2023-02-25 07:19:30.425509: [NET] peer(zxCt…SZTk) - Received handshake response
2023-02-25 07:19:30.438342: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:19:57.434074: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:19:57.434216: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:20:19.417985: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:20:37.955773: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:21:07.644804: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:21:33.419152: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:21:45.430279: [NET] peer(zxCt…SZTk) - Sending handshake initiation
2023-02-25 07:21:45.441441: [NET] peer(zxCt…SZTk) - Received handshake response
2023-02-25 07:21:45.441614: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:21:55.854015: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:22:22.755301: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:22:22.755374: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:22:49.438533: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:22:49.438737: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:23:15.810006: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:23:15.810270: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:23:42.873107: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:23:42.873381: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:24:09.215931: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:24:14.490570: [NET] peer(zxCt…SZTk) - Sending handshake initiation
2023-02-25 07:24:14.503199: [NET] peer(zxCt…SZTk) - Received handshake response
2023-02-25 07:24:14.503357: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:24:28.462521: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:24:54.473497: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:24:54.474120: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:25:20.838751: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:25:20.838751: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:25:47.197302: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:25:55.604617: [NET] Network change detected with unsatisfied route and interface order [en0, utun7, pdp_ip0]
2023-02-25 07:25:55.604678: [NET] Connectivity offline, pausing backend.
2023-02-25 07:25:55.604741: [NET] Device closing
2023-02-25 07:25:55.604811: [NET] Routine: TUN reader - stopped
2023-02-25 07:25:55.604865: [NET] Routine: event worker - stopped
2023-02-25 07:25:55.604935: [NET] Routine: receive incoming v4 - stopped
2023-02-25 07:25:55.604979: [NET] Routine: receive incoming v6 - stopped
2023-02-25 07:25:55.605039: [NET] peer(zxCt…SZTk) - Stopping
2023-02-25 07:25:55.605117: [NET] peer(zxCt…SZTk) - Routine: sequential receiver - stopped
2023-02-25 07:25:55.605153: [NET] peer(zxCt…SZTk) - Routine: sequential sender - stopped
2023-02-25 07:25:55.605209: [NET] Routine: decryption worker 2 - stopped
2023-02-25 07:25:55.605181: [NET] Device closed
2023-02-25 07:25:55.605232: [NET] Routine: decryption worker 4 - stopped
2023-02-25 07:25:55.605232: [NET] Routine: decryption worker 6 - stopped
2023-02-25 07:25:55.605319: [NET] Routine: handshake worker 2 - stopped
2023-02-25 07:25:55.605705: [NET] Routine: decryption worker 3 - stopped
2023-02-25 07:25:55.605770: [NET] Routine: handshake worker 4 - stopped
2023-02-25 07:25:55.605886: [NET] Routine: handshake worker 6 - stopped
2023-02-25 07:25:55.605955: [NET] Routine: handshake worker 3 - stopped
2023-02-25 07:25:55.606082: [NET] Routine: decryption worker 1 - stopped
2023-02-25 07:25:55.606157: [NET] Routine: handshake worker 5 - stopped
2023-02-25 07:25:55.606225: [NET] Routine: decryption worker 5 - stopped
2023-02-25 07:25:55.605652: [NET] Routine: handshake worker 1 - stopped
2023-02-25 07:25:55.607126: [NET] Routine: encryption worker 6 - stopped
2023-02-25 07:25:55.607192: [NET] Routine: encryption worker 3 - stopped
2023-02-25 07:25:55.607256: [NET] Routine: encryption worker 4 - stopped
2023-02-25 07:25:55.607319: [NET] Routine: encryption worker 5 - stopped
2023-02-25 07:25:55.607384: [NET] Routine: encryption worker 2 - stopped
2023-02-25 07:25:55.607481: [NET] Routine: encryption worker 1 - stopped
2023-02-25 07:25:55.775363: [NET] Network change detected with unsatisfied route and interface order [en0, utun7, pdp_ip0]
2023-02-25 07:25:55.937151: [NET] Network change detected with satisfied route and interface order [pdp_ip0, utun7]
2023-02-25 07:25:55.937275: [NET] Connectivity online, resuming backend.
2023-02-25 07:25:56.342613: [NET] DNS64: mapped <My Home IPv4 Address> to 2607:7700:0:1b:0:1:68ae:4322
2023-02-25 07:25:56.343575: [NET] Attaching to interface
2023-02-25 07:25:56.343821: [NET] Routine: encryption worker 1 - started
2023-02-25 07:25:56.343823: [NET] Routine: decryption worker 1 - started
2023-02-25 07:25:56.343823: [NET] Routine: handshake worker 1 - started
2023-02-25 07:25:56.343877: [NET] Routine: decryption worker 4 - started
2023-02-25 07:25:56.343879: [NET] UAPI: Updating private key
2023-02-25 07:25:56.343874: [NET] Routine: handshake worker 5 - started
2023-02-25 07:25:56.343919: [NET] Routine: decryption worker 6 - started
2023-02-25 07:25:56.343935: [NET] Routine: encryption worker 6 - started
2023-02-25 07:25:56.343978: [NET] Routine: encryption worker 2 - started
2023-02-25 07:25:56.344011: [NET] Routine: handshake worker 4 - started
2023-02-25 07:25:56.344018: [NET] Routine: encryption worker 5 - started
2023-02-25 07:25:56.344072: [NET] Routine: encryption worker 3 - started
2023-02-25 07:25:56.344114: [NET] Routine: decryption worker 3 - started
2023-02-25 07:25:56.344133: [NET] Routine: handshake worker 6 - started
2023-02-25 07:25:56.344161: [NET] Routine: decryption worker 2 - started
2023-02-25 07:25:56.344198: [NET] Routine: handshake worker 3 - started
2023-02-25 07:25:56.344205: [NET] Routine: decryption worker 5 - started
2023-02-25 07:25:56.344269: [NET] Routine: handshake worker 2 - started
2023-02-25 07:25:56.344282: [NET] Routine: encryption worker 4 - started
2023-02-25 07:25:56.344332: [NET] Routine: TUN reader - started
2023-02-25 07:25:56.344367: [NET] Routine: event worker - started
2023-02-25 07:25:56.344459: [NET] UAPI: Updating listen port
2023-02-25 07:25:56.344518: [NET] UAPI: Removing all peers
2023-02-25 07:25:56.344953: [NET] peer(zxCt…SZTk) - UAPI: Created
2023-02-25 07:25:56.345013: [NET] peer(zxCt…SZTk) - UAPI: Updating endpoint
2023-02-25 07:25:56.345138: [NET] peer(zxCt…SZTk) - UAPI: Updating persistent keepalive interval
2023-02-25 07:25:56.345226: [NET] peer(zxCt…SZTk) - UAPI: Removing all allowedips
2023-02-25 07:25:56.345305: [NET] peer(zxCt…SZTk) - UAPI: Adding allowedip
2023-02-25 07:25:56.345394: [NET] peer(zxCt…SZTk) - UAPI: Adding allowedip
2023-02-25 07:25:56.345677: [NET] UDP bind has been updated
2023-02-25 07:25:56.345695: [NET] Routine: receive incoming v4 - started
2023-02-25 07:25:56.345731: [NET] peer(zxCt…SZTk) - Starting
2023-02-25 07:25:56.345745: [NET] Routine: receive incoming v6 - started
2023-02-25 07:25:56.345897: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:25:56.345924: [NET] peer(zxCt…SZTk) - Routine: sequential sender - started
2023-02-25 07:25:56.345932: [NET] peer(zxCt…SZTk) - Routine: sequential receiver - started
2023-02-25 07:25:56.345964: [NET] peer(zxCt…SZTk) - Sending handshake initiation
2023-02-25 07:25:56.347008: [NET] Interface state was Down, requested Up, now Up
2023-02-25 07:25:56.347068: [NET] Device started
2023-02-25 07:25:56.347750: [NET] Network change detected with satisfied route and interface order [pdp_ip0, utun7]
2023-02-25 07:25:56.348809: [NET] DNS64: mapped <My Home IPv4 Address> to 2607:7700:0:1b:0:1:68ae:4322
2023-02-25 07:25:56.348899: [NET] peer(zxCt…SZTk) - UAPI: Updating endpoint
2023-02-25 07:25:56.349099: [NET] Routine: receive incoming v4 - stopped
2023-02-25 07:25:56.349188: [NET] Routine: receive incoming v6 - stopped
2023-02-25 07:25:56.349429: [NET] UDP bind has been updated
2023-02-25 07:25:56.349454: [NET] Routine: receive incoming v4 - started
2023-02-25 07:25:56.349489: [NET] Routine: receive incoming v6 - started
2023-02-25 07:25:56.405904: [NET] peer(zxCt…SZTk) - Received handshake response
2023-02-25 07:25:58.343054: [NET] Network change detected with satisfied route and interface order [pdp_ip0, utun7]
2023-02-25 07:25:58.344785: [NET] DNS64: mapped <My Home IPv4 Address> to 2607:7700:0:1b:0:1:68ae:4322
2023-02-25 07:25:58.345046: [NET] peer(zxCt…SZTk) - UAPI: Updating endpoint
2023-02-25 07:25:58.345325: [NET] Routine: receive incoming v4 - stopped
2023-02-25 07:25:58.345466: [NET] Routine: receive incoming v6 - stopped
2023-02-25 07:25:58.345820: [NET] UDP bind has been updated
2023-02-25 07:25:58.345851: [NET] Routine: receive incoming v4 - started
2023-02-25 07:25:58.345935: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:25:58.346015: [NET] Routine: receive incoming v6 - started
2023-02-25 07:26:48.794934: [NET] Network change detected with satisfied route and interface order [pdp_ip0, utun7]
2023-02-25 07:26:48.796476: [NET] DNS64: mapped <My Home IPv4 Address> to 2607:7700:0:1b:0:1:68ae:4322
2023-02-25 07:26:48.796866: [NET] peer(zxCt…SZTk) - UAPI: Updating endpoint
2023-02-25 07:26:48.797182: [NET] Routine: receive incoming v4 - stopped
2023-02-25 07:26:48.797315: [NET] Routine: receive incoming v6 - stopped
2023-02-25 07:26:48.797693: [NET] UDP bind has been updated
2023-02-25 07:26:48.797731: [NET] Routine: receive incoming v4 - started
2023-02-25 07:26:48.797753: [NET] Routine: receive incoming v6 - started
2023-02-25 07:26:48.798196: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:26:49.775855: [NET] Network change detected with satisfied route and interface order [pdp_ip0, utun7]
2023-02-25 07:26:49.777424: [NET] DNS64: mapped <My Home IPv4 Address> to 2607:7700:0:1b:0:1:68ae:4322
2023-02-25 07:26:49.777785: [NET] peer(zxCt…SZTk) - UAPI: Updating endpoint
2023-02-25 07:26:49.778087: [NET] Routine: receive incoming v4 - stopped
2023-02-25 07:26:49.778303: [NET] Routine: receive incoming v6 - stopped
2023-02-25 07:26:49.778714: [NET] UDP bind has been updated
2023-02-25 07:26:49.778780: [NET] Routine: receive incoming v6 - started
2023-02-25 07:26:49.778773: [NET] Routine: receive incoming v4 - started
2023-02-25 07:26:49.778825: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:27:00.976307: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:27:01.346342: [NET] Network change detected with satisfied route and interface order [pdp_ip0, utun7]
2023-02-25 07:27:01.347931: [NET] DNS64: mapped <My Home IPv4 Address> to 2607:7700:0:1b:0:1:68ae:4322
2023-02-25 07:27:01.348256: [NET] peer(zxCt…SZTk) - UAPI: Updating endpoint
2023-02-25 07:27:01.348546: [NET] Routine: receive incoming v4 - stopped
2023-02-25 07:27:01.348634: [NET] Routine: receive incoming v6 - stopped
2023-02-25 07:27:01.348984: [NET] UDP bind has been updated
2023-02-25 07:27:01.349007: [NET] Routine: receive incoming v4 - started
2023-02-25 07:27:01.349037: [NET] Routine: receive incoming v6 - started
2023-02-25 07:27:01.349107: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:27:01.979176: [NET] Network change detected with satisfied route and interface order [pdp_ip0, utun7]
2023-02-25 07:27:01.980783: [NET] DNS64: mapped <My Home IPv4 Address> to 2607:7700:0:1b:0:1:68ae:4322
2023-02-25 07:27:01.981014: [NET] peer(zxCt…SZTk) - UAPI: Updating endpoint
2023-02-25 07:27:01.981337: [NET] Routine: receive incoming v4 - stopped
2023-02-25 07:27:01.981445: [NET] Routine: receive incoming v6 - stopped
2023-02-25 07:27:01.981851: [NET] UDP bind has been updated
2023-02-25 07:27:01.981975: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:27:01.982070: [NET] Routine: receive incoming v6 - started
2023-02-25 07:27:01.982062: [NET] Routine: receive incoming v4 - started
2023-02-25 07:27:20.758974: [NET] peer(zxCt…SZTk) - Retrying handshake because we stopped hearing back after 15 seconds
2023-02-25 07:27:20.759163: [NET] peer(zxCt…SZTk) - Sending handshake initiation
2023-02-25 07:27:20.876593: [NET] peer(zxCt…SZTk) - Received handshake response
2023-02-25 07:27:20.876848: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:28:46.181838: [NET] Network change detected with satisfied route and interface order [pdp_ip0, utun7]
2023-02-25 07:28:46.182575: [NET] DNS64: mapped <My Home IPv4 Address> to 2607:7700:0:1b:0:1:68ae:4322
2023-02-25 07:28:46.182720: [NET] peer(zxCt…SZTk) - UAPI: Updating endpoint
2023-02-25 07:28:46.182840: [NET] Routine: receive incoming v4 - stopped
2023-02-25 07:28:46.182873: [NET] Routine: receive incoming v6 - stopped
2023-02-25 07:28:46.183035: [NET] UDP bind has been updated
2023-02-25 07:28:46.183068: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:28:46.183078: [NET] Routine: receive incoming v4 - started
2023-02-25 07:28:46.183102: [NET] Routine: receive incoming v6 - started
2023-02-25 07:28:48.460821: [NET] peer(zxCt…SZTk) - Received handshake initiation
2023-02-25 07:28:48.461020: [NET] peer(zxCt…SZTk) - Sending handshake response
2023-02-25 07:28:48.530865: [NET] peer(zxCt…SZTk) - Receiving keepalive packet
2023-02-25 07:28:49.729507: [NET] Network change detected with satisfied route and interface order [pdp_ip0, utun7]
2023-02-25 07:28:49.731090: [NET] DNS64: mapped <My Home IPv4 Address> to 2607:7700:0:1b:0:1:68ae:4322
2023-02-25 07:28:49.731259: [NET] peer(zxCt…SZTk) - UAPI: Updating endpoint
2023-02-25 07:28:49.731542: [NET] Routine: receive incoming v4 - stopped
2023-02-25 07:28:49.731646: [NET] Routine: receive incoming v6 - stopped
2023-02-25 07:28:49.731869: [NET] UDP bind has been updated
2023-02-25 07:28:49.731922: [NET] peer(zxCt…SZTk) - Sending keepalive packet
2023-02-25 07:28:49.732018: [NET] Routine: receive incoming v4 - started
Soon after connecting, I start getting connection errors on my phone/connected device.
In my logs, I see things that look like IPv6 address mapping going on, but IPv6 is disabled on the Brume 2 (due to the warnings about leakage). I have IPv6 enabled on the rest of my home network, so maybe that is the issue. I’m not sure.