I'll tell you what my configuration is like.
At home I have an ASUS router with the Wireguard server and ADGUARD HOME installed. I want to link the X750 as a client and that all the devices connected to the X750 go out through the ASUS server.
admon
August 13, 2024, 10:48am
2
This won't be possible because the real IP is only known on the X750 - not on the ASUS.
But I need that because I have in ADH filters for different devices and if the real IP is unknown It can not be applied. I have marked "SHOW real IP" but it doesnt work.
admon
August 13, 2024, 11:14am
4
This might only work if every device connects itself via WireGuard to the ASUS.
So I have to forget the option site-to-site to join X750 with asus by wireguard?
In that case, when I am connected to X750 wifi, my device client by x750 4G connect to server wireguard (asus in my home) and then comeback to navegate trought 4G X750 ????
slesar
August 13, 2024, 5:18pm
6
You have one client wireguard and result one devise. @admon said make wireguard more clients. So 4 clients wireguard.
Another option your Asus make open dns resolver but danger for you.
All connections go out trough adguard home. I have made a profile (filter navigation) for each device. One for adults and other for my children.
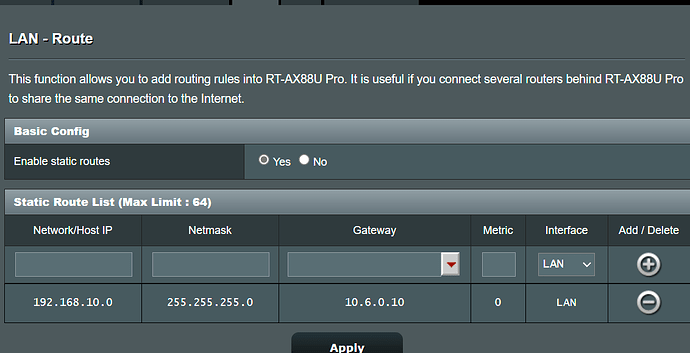
But, If I have only one IP (10.6.0.10) I can not apply the rules.
And I dont understand why if I am under the wifi of GL-X750 the conetion can not be direct.
slesar
August 13, 2024, 7:54pm
8
Try rasbeprry pi for mini server to make Adguard home and connect to gl 4g router. Copy filters from Asus to rasberry pi. Problem solved
I dont understand how it should be so difficult. Join two nets by VPN tunnel.
admon
August 13, 2024, 8:16pm
10
Because both routers will do NAT by default. That is what consumer devices do because consumers don't need S2S VPN.
So you will need to disable NAT on both VPN interfaces.
1 Like
That´s what I want.
admon
August 14, 2024, 7:31am
12
You will need to disable MASQ per Zone:https://openwrt.org/docs/guide-user/firewall/firewall_configuration?s=masq#zones
I can't really help you with this, so you might just try it. I am not sure if the GL firmware will respect this change or might revert it later.
bruce
August 14, 2024, 9:12am
13
Hi, atorcha
I found you have contacted the support team colleague from the email, and we have provided the solution for you, including how to config the VPN server. This solution is supposed to be achieved this special requirement. Thanks.
admon
August 14, 2024, 10:16am
14
@Bruce , might you be able to post the solution found by support?
I guess it could be useful for other people as well.
bruce
August 14, 2024, 11:20am
15
Our solution bases on the GL router, including the VPN Server and Client. Only for reference.
Enable Lan Access on the server and client. Disbale IP masq on the client. And configure the server to route to the client's subnet.
In the client, DNS is configured as the wg server's address, and custom DNS override vpn dns is turned off.
The server firewall is configured with a redirection rule that redirects traffic from port 53 of the wgserver to port 3053 (adguard).
The client subnet DNS traffic will be directed to server. Client Luci add firewall rule: iptables -w -t nat -I PREROUTING -i br-lan -p udp --dport 53 -j DNAT --to 10.0.0.1
restart the firewall and restarts the VPN.
Update:
1 Like
atorcha
August 14, 2024, 12:23pm
16
Sorry but it still does not work.
root@GL-X750:~# uci export network
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd52:4828:3011::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
config device
option name 'eth1'
option macaddr '94:83:c4:50:0a:c3'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option isolate '0'
option ipaddr '192.168.10.1'
config device
option name 'eth0'
option macaddr '94:83:c4:50:0a:c2'
config interface 'wan'
option device 'eth0'
option proto 'dhcp'
option force_link '0'
option ipv6 '0'
option classlessroute '0'
config interface 'wan6'
option proto 'dhcpv6'
option disabled '1'
option device '@wan'
config interface 'tethering6'
option proto 'dhcpv6'
option disabled '1'
option device '@tethering'
config interface 'wwan6'
option proto 'dhcpv6'
option disabled '1'
option device '@wwan'
config interface 'guest'
option force_link '1'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.9.1'
option netmask '255.255.255.0'
option ip6assign '60'
option multicast_querier '1'
option igmp_snooping '0'
option isolate '0'
option bridge_empty '1'
option disabled '1'
config interface 'wwan'
option proto 'dhcp'
option classlessroute '0'
config interface 'modem_1_1_2_6'
option proto 'dhcpv6'
option disabled '1'
option device '@modem_1_1_2'
config rule 'policy_direct_rt'
option lookup 'main'
option suppress_prefixlength '0'
option priority '1100'
config rule 'policy_default_rt_vpn'
option mark '0x8000/0xc000'
option lookup '8000'
option priority '1101'
option invert '1'
config rule6 'policy_direct_rt6'
option lookup 'main'
option suppress_prefixlength '0'
option priority '1100'
config rule6 'policy_default_rt_vpn6'
option mark '0x8000/0xc000'
option lookup '8000'
option priority '1101'
option invert '1'
config rule 'policy_default_rt_vpn_ts'
option lookup 'main'
option priority '1099'
option mark '0x80000/0xc0000'
option invert '0'
config interface 'modem_1_1_2'
option apn 'airtelwap.es'
option proto 'qmi'
option device '/dev/cdc-wdm0'
option node '1-1.2:1.4'
option username 'wap@wap'
option password 'wap125'
option metric '40'
option roaming '1'
option band_enable '0'
option disabled '0'
config interface 'wgclient'
option proto 'wgclient'
option config 'peer_2001'
option disabled '0'
root@GL-X750:~# wg show
interface: wgclient
public key: xxxxxawwm+KbjzExxxxxx9ArpBco8nRw=
private key: (hidden)
listening port: 51323
fwmark: 0x8000
peer: xxxxxxxM=
endpoint: xx.xx.216.231:51820
allowed ips: 0.0.0.0/0
latest handshake: 1 minute, 7 seconds ago
transfer: 352.23 KiB received, 450.72 KiB sent
persistent keepalive: every 25 seconds
root@GL-X750:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'guest'
option network 'guest'
option output 'ACCEPT'
option input 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
list network 'wwan'
list network 'modem_1_1_2'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option input 'DROP'
config zone 'wgclient'
option name 'wgclient'
option output 'ACCEPT'
option mtu_fix '1'
option network 'wgclient'
option input 'ACCEPT'
option masq6 '0'
option forward 'DROP'
option enabled '1'
option masq '0'
config forwarding
option src 'lan'
option dest 'wan'
option enabled '0'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include 'nat6'
option path '/etc/firewall.nat6'
option reload '1'
config rule 'block_dns'
option name 'block_dns'
option src '*'
option dest_port '53'
option target 'REJECT'
option device 'br-*'
option enabled '0'
config include 'gls2s'
option type 'script'
option path '/var/etc/gls2s.include'
option reload '1'
config include 'glblock'
option type 'script'
option path '/usr/bin/gl_block.sh'
option reload '1'
config forwarding
option src 'guest'
option dest 'wan'
option enabled '0'
config rule
option name 'Allow-DHCP'
option src 'guest'
option target 'ACCEPT'
option proto 'udp'
option dest_port '67-68'
config rule
option name 'Allow-DNS'
option src 'guest'
option target 'ACCEPT'
option proto 'tcp udp'
option dest_port '53'
config include 'vpn_server_policy'
option type 'script'
option path '/etc/firewall.vpn_server_policy.sh'
option reload '1'
option enabled '1'
config forwarding 'wgclient2wan'
option src 'wgclient'
option dest 'wan'
option enabled '1'
config forwarding 'lan2wgclient'
option src 'lan'
option dest 'wgclient'
option enabled '1'
config forwarding 'guest2wgclient'
option src 'guest'
option dest 'wgclient'
option enabled '1'
config forwarding 'wgclient2lan'
option src 'wgclient'
option dest 'lan'
option enabled '1'
config forwarding
option dest 'guest'
option src 'wgclient'
config rule 'glservice_https'
option name 'glservice_https'
option dest_port '443'
option proto 'tcp udp'
option src 'wan'
option target 'ACCEPT'
option enabled '1'
root@GL-X750:~#
j2zero
August 14, 2024, 3:26pm
17
I dont found where to write that...
I can access to all devices connected to GL-750 from ASUS but teh oonly problem is that ADH only have one client (10.6.0.10)
j2zero
August 14, 2024, 4:37pm
19
I see your version of openwrt is a newer release compared to my firmware. I'm not sure where you enter the custom rules on your firmware, I think you might need to edit a file directly. @bruce where should the code go?