Hello everyone,
I’m currently using a MUDI router, and in general I’m quite happy with it.
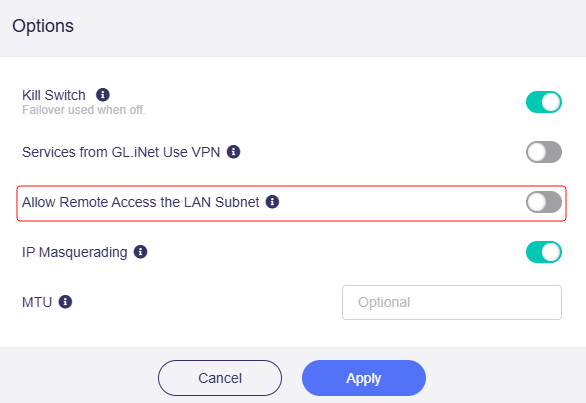
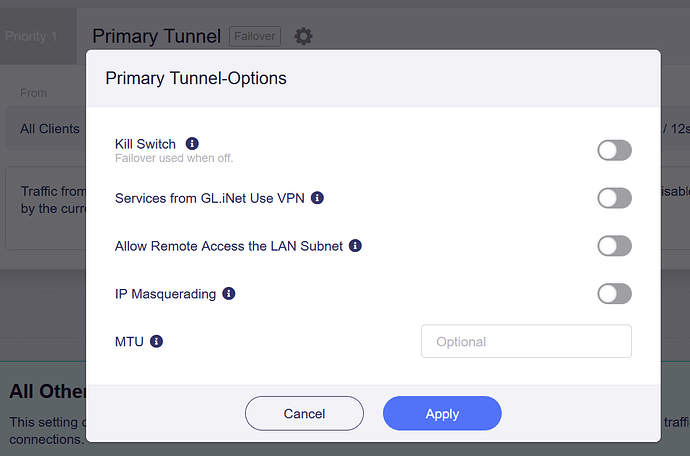
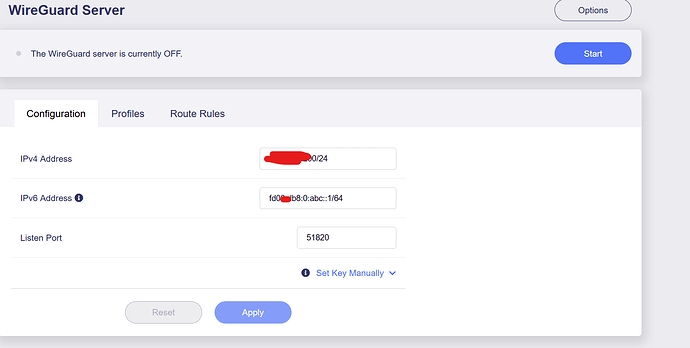
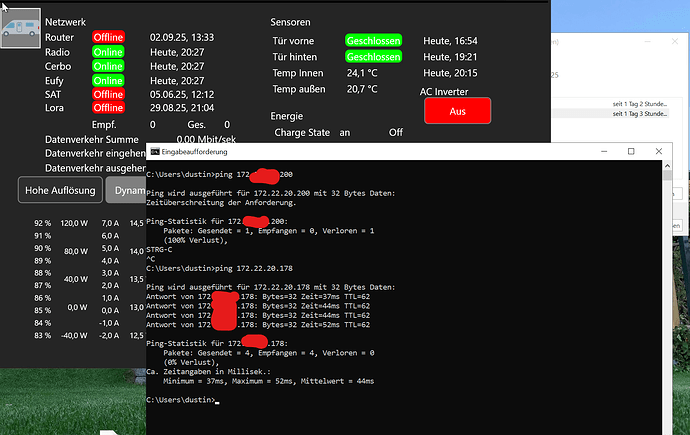
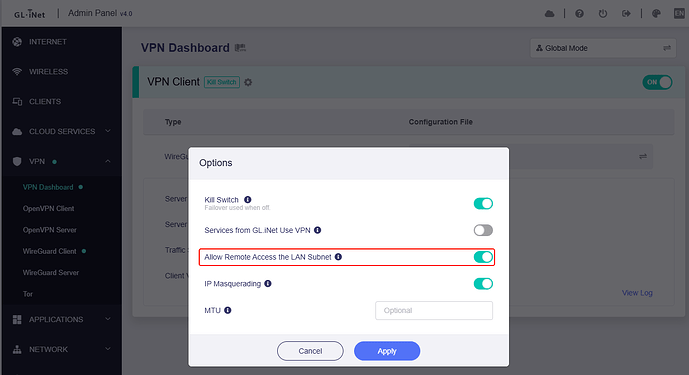
However, I noticed that it sometimes loses the Wireguard connection configured in LUCI.
My setup:
- GL.iNet with LUCI
- LUCI firewall rules
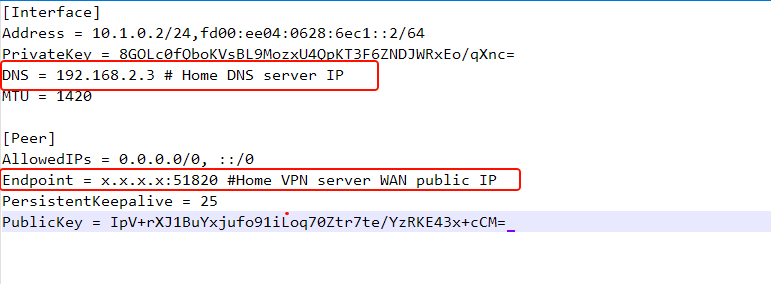
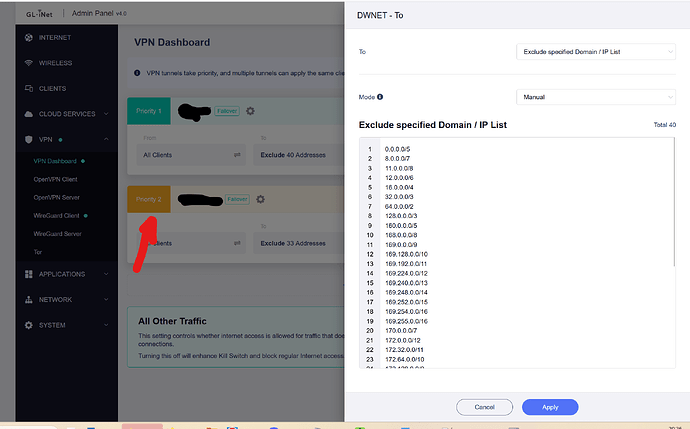
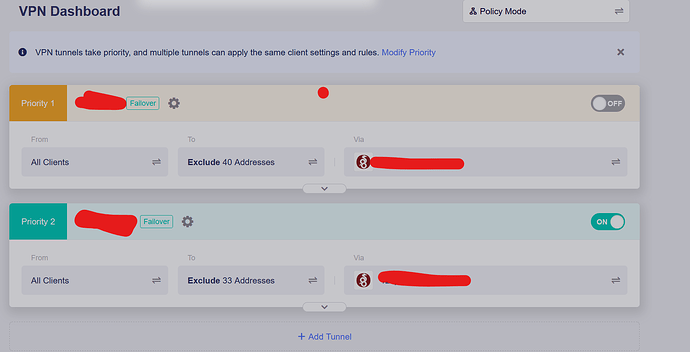
- LUCI Wireguard to Mikrotik Router 1
- LUCI Wireguard to Mikrotik Router 2
When the tunnel drops, I usually have to either restart the router or restart Wireguard manually in LUCI.
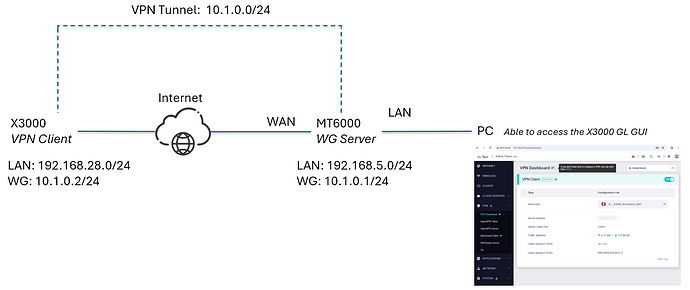
Now, I’d like to install the X3000 in my motorhome. Most of the time it just sits parked but should still remain online. Currently, a Mikrotik router is doing this job without issues.
My question:
Does anyone have a script that checks if the Wireguard tunnels are online (e.g. via ping to the remote endpoint), and if not:
- after 20 seconds offline → restart the tunnel
- after 10 minutes offline → reboot the whole router
Also, in which folder should such a script be placed so it survives firmware updates?
Without something like this, I can’t really replace the Mikrotik, since Wireguard there runs 100% stable.
Thanks in advance!