Hi, If you upgrade to beta firmware 3.022 and above you will find VPN policy settings.
Here is a quick guide.
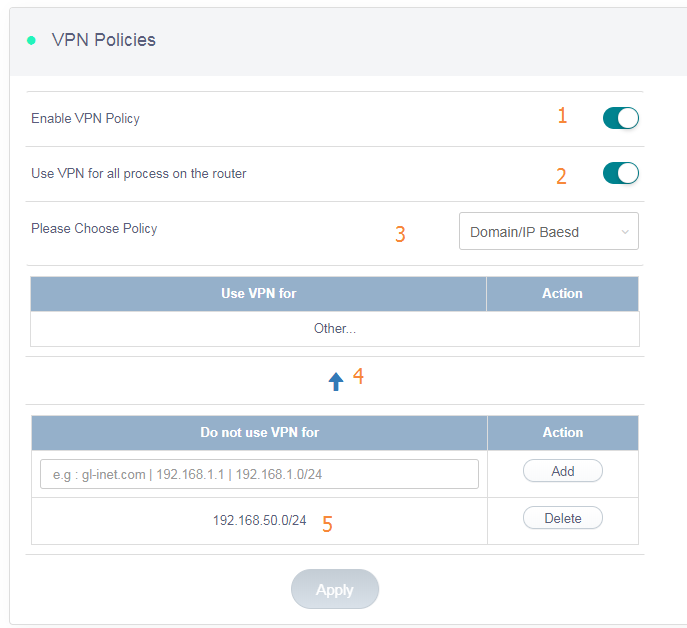
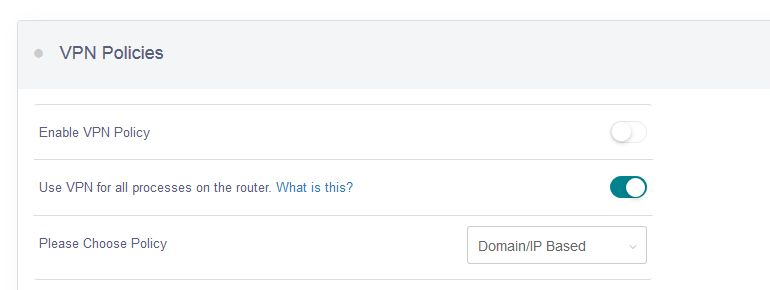
- Enable or Disable VPN policy
- If you enable this, all the processes on the router will use vpn. It means the router’s public IP will be VPN server’s IP. Your DDNS will be your VPN server. If you disable this, only the clients connected to the router will go to the VPN.
- You can choose Domain/IP based policy or MAC based policy. You can only choose one but not mixed. We tried to make mixed policy and it will make the logic hard to understand.
- Clicking this you will choose whether you need to bypass a list or forward a list to vpn. For example in the picture use VPN for all domain/IP but not 192.168.50.0/24. By using this, I can still access all my service on 192.168.50.0/24 subnet, for example a local share or printer. Using this option, you can also achieve the scenario like only use VPN for facebook, Netflix etc.
- You can use subnet instead of individual IP address.
You have to click APPLY to make this take effect.
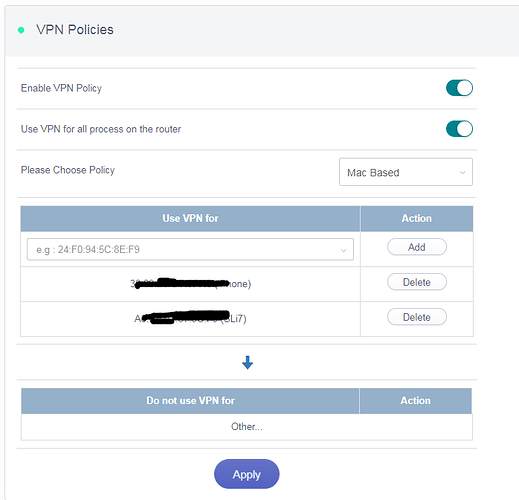
You can also set up MAC address based policy. Using this you will be able to achieve scenario like “only allowing your TV box to use VPN” or only the TV box don’t use VPN.
Pls test and report here. Thanks very much!